What is SNMP?
SNMP stands for Simple Network Management Protocol and is a widespread protocol for monitoring network devices. It is not just a monitoring protocol. As the name implies, it also allows for managing and configuring a network. It can be used to detect errors and generate alerts of network issues, almost in real time.
Developed in the mid 1980s, SNMP gradually became the de-facto standard in network monitoring by the 1990s and into the early 2000s. It is still in common use thanks to its relative simplicity and large range of metrics that can be collected for monitoring. It is not without its shortcomings, and the three versions of the protocol that were developed to address them were not completely successful.
Nowadays, most network devices support SNMP by default, without the network administrator having to do anything other than use an SNMP monitoring tool.
What are the components of SNMP?
SNMP works with two main components: an SNMP agent and an SNMP manager. The agent is installed on the device to be monitored and consists of a small application that collects metrics locally to send to a remote location. The SNMP manager is on the receiving end. A series of commands can be used on the manager’s side to retrieve info from the agent. The agent itself can, when necessary, send info in the form of SNMP traps, one of the most well-known features of the SNMP protocol. How SNMP works is basically as a protocol for collecting metrics and allowing a remote agent and a manager to exchange them in a structured way.
Agent and manager communicate through one of the three versions of SNMP. Depending on the version, different settings have to be configured. The configuration of SNMP is not complex, considering its age. The question “what is SNMP” can mostly be answered by explaining that it is a protocol to monitor and maintain network devices through the use of an agent and a manager. But there is more to it.
What is an SNMP agent?
The SNMP agent is the software component responsible for responding to queries, carrying out requests, and issuing traps. Mainly, an SNMP agent has three tasks. The first is to reply to an SNMP get from the manager, which is a type of query to get information about the managed device. Similarly, as the second task, an SNMP manager can also issue a set query to manage or configure the managed device or, alternatively, to an SNMP agent, which then carries the request to the host it is present on.
Finally, there is the trap signal that the agent can issue to the manager to communicate if an error condition has occurred. Therefore, an SNMP agent is not just a passive application waiting for the manager, because it can also actively send back information whenever reputed necessary or configured to do so. An SNMP agent is therefore the core of the SNMP protocol by virtue of collecting metrics and signaling errors back to the SNMP manager.
What is an SNMP manager?
The SNMP manager is at the other end of an SNMP setup relative to the agent. SNMP managers are generally installed on an NMS (Network Management Station), of which there may be multiple instances per network depending on the number of managed devices.
An SNMP manager takes care of the monitoring and related computational tasks. The hardware resources that are needed for it to run are thus higher than for an agent. While SNMP can be used directly from the command line, nowadays monitoring tools with dashboards and automated queries are more commonly implemented as SNMP managers. While an SNMP agent is a small piece with rather fixed functionalities, an SNMP manager can be complex software that supports SNMP queries, but it is not limited to them only.
What is an SNMP device?
An SNMP device is where an SNMP agent is installed. These devices include switches, bridges, routers, access servers, hubs, printers, and general hosts. The list is partial, SNMP is ubiquitous and easily installed almost anywhere. The SNMP agent often comes pre-installed by vendors on network devices.
Therefore, any device can become an SNMP device after the simple installation of an agent. SNMP is well-supported and available for all major operating systems, even including Android and iOS.
What SNMP versions are available?
SNMP originated during the early 1980s from a group of collaborators who viewed the efforts at the time as both unimplementable and unworkable. So SNMP has a long history, spanning over three decades. During these years, multiple versions of the protocol have been released. The original, v1, has mostly disappeared from all modern infrastructures, unless a specific device could not be upgraded to SNMP v2.
The main issue that v1 did not solve was security. It essentially had no security at all, leaving it to the underlying channels over which the SNMP messages were sent.
SNMP v2, particularly its slightly more secure variant v2c, is by far the most popular to this day. It came out in 1993 and added new commands as well as a party-based security system that did not catch on. SNMP v2c succeeded by introducing a simpler community-based security scheme and 64-bit counters (the original SNMP had 32-bit only).
Parallel to SNMP v2c, v2u was developed as a compromise that offered better security than v1 while being less complex than v2. Although it was not used much, it was an important inspiration for v3.
SNMP v2, and all its variants, are not compatible with v1 since the messages use a different header and protocol data formats.
Version 3 came in the early 2000s with support for cryptography and a plethora of different concepts, conventions, and terminologies. However, the core protocol was not changed much, and many vendors preferred to remain on the more tested and less computational-heavy v2 and v2c.
What is SNMP used for?
SNMP is largely used for IT monitoring. With SNMP monitoring, it is possible to keep an eye on important parameters for switches, access points, and routers, as well as the many other types of devices that SNMP is often installed on. These include appliances, hardware sensors, and printers, which makes SNMP a complete solution for hardware monitoring.
The capabilities of the SNMP protocol go beyond just monitoring. After all, what SNMP stands for is Simple Network Management Protocol, so management is also possible with it. Remotely managing and configuring devices is one of the main uses of SNMP. With a simple SNMP client or monitoring tool, parameters and options can be changed remotely via SNMP on many devices.
How does SNMP work?
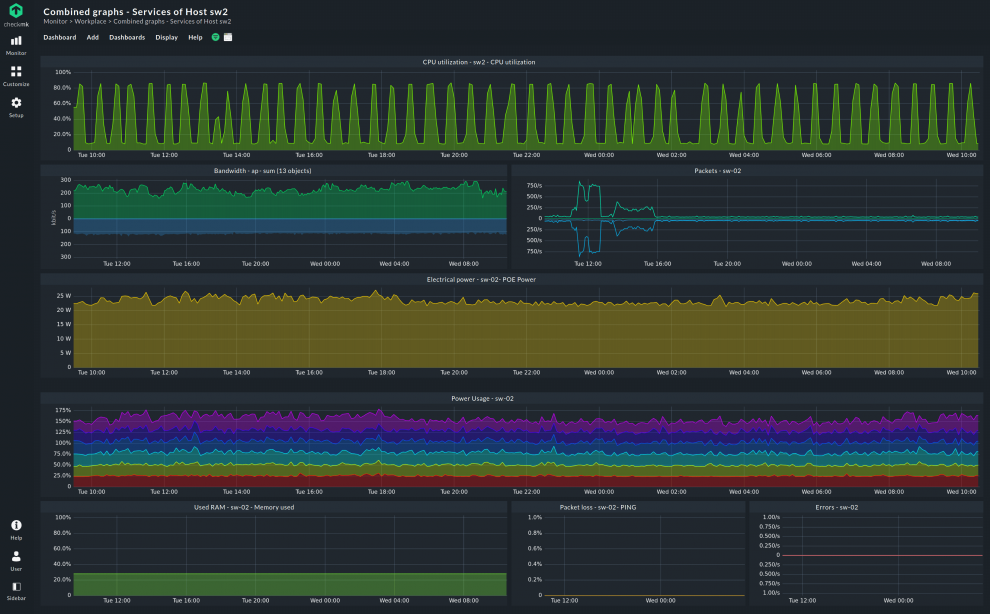
Setting up SNMP monitoring is normally a low effort task. Since plenty of devices come with an SNMP agent already installed, it only needs to be activated to start monitoring the device. To activate the agent, you configure it to accept active requests, mostly SNMP get and set commands. However, it is usually best to refer to the individual device’s manual first since vendors have different implementations of the protocol.
Once the agents are activated, the monitoring solution of choice can now retrieve information and metrics on the device via SNMP. Often, this is accomplished through a complete pull of all SNMP data on the managed devices, an SNMP walk command. How and what is pulled depends on the operator or the monitoring tool. For example, Checkmk uses service discovery through SNMP by retrieving only the very first records (OIDs) on a device. Based on this information, further queries are made as required. This avoids the need to first transfer large quantities of data and this considerably speeds up the discovery step for SNMP devices, which can take hours on large infrastructures.
Once all is discovered and the agents active, the actual monitoring can take place. The managed devices are ready to listen for the manager requesting metrics. The collection of these metrics happens on the agent-side, after which they are sent over the network for the manager to analyze them. Occasionally, an agent may send a trap back to the manager, but most of the time it is the manager that asks the agents for data.
What is OID in SNMP?
OID (Object Identifier) is an identifier mechanism for naming any type of object or concept. It is an international standard for addressing anything in a very specific way. SNMP adopted the concept, but did not originate it.
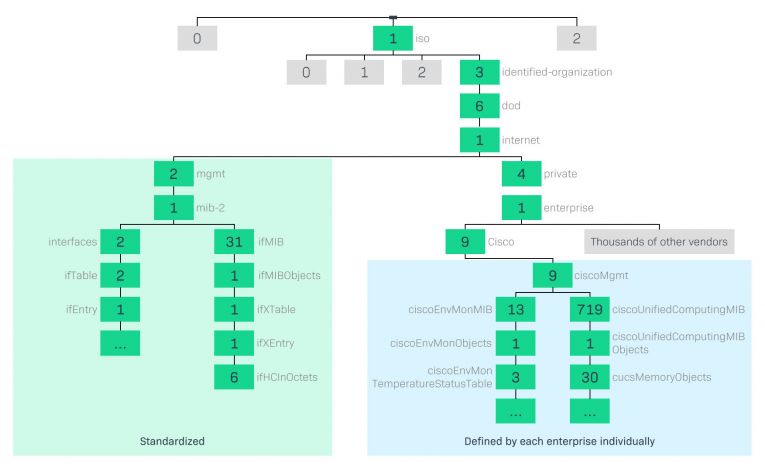
An SNMP OID is a long sequence of numbers separated by dots. For instance, 1.3.6.1.2.2.1.5 is an OID that unequivocally identifies with an object in a hierarchical logical tree. OIDs should be read from left to right, starting at the root which can only be either 0 or 1 or 2, depending on the arc of the following standards:
- 0 is for ITU-T (one of the three sectors of the International Telecommunication Union).
- 1 is for ISO (International Organization for Standardization).
- 2 is for a joint ISO/ITU-T arc.
Both organizations define child nodes, the subsequent numbers, respectively, and may delegate assigning authority to others.
In the example above, the 1 is for ISO, the 3 for “identified organization”, the 6 for the American Department of Defense and down through the tree to the very last digit that addresses a specific “thing”, depending on the context. This thing is often a variable that identifies a metric specific to the device that is monitored. It can be the temperature of a processor, for instance, or the uptime of a host.
Some subtrees are generic, others belong to specific organizations or companies and specify their product. Those are monitored by SNMP, which makes the OID vital for knowing what and where every device supporting SNMP is. Each vendor is free to specify their own subtrees, depending on their devices and what they do.
These long series of numbers would be of scarce usefulness if it was not possible to retrieve what each number means. To do so, another piece of how SNMP works is used, the MIB (Management Information Base).
What is MIB in SNMP?
A MIB in SNMP translates OIDs into human-readable form by providing names, definitions, and descriptions for the values. As each vendor has a different classification for their own OID subtrees, a MIB comes as a table that is used to group instances of a tabular object.
Rows are present in each MIB and each of them represents a series of information or settings belonging to an object. For instance, a row may contain a name, type, and current temperature of a hardware sensor; another may include the number of hardware ports, the max and current speed of each, and the firmware version in a switch. The more complex the device, the more digits are used to index all its features, metrics, and settings.
Every vendor maintains and updates their MIBs. These are human-readable dictionaries that match the OIDs specific to the device in question. The protocol only needs OIDs to function, the MIBs are mostly there to inform network administrators of what is to be found at every OID.
SNMP get
SNMP get is the simplest operation done in SNMP monitoring. The SNMP manager uses the get command to retrieve information from the agent by specifying the OID of what should be retrieved. An OID can be obtained for each SNMP get command, retrieving a single metric on each sweep.
Depending on the version of the SNMP protocol used, a community string may also be necessary to authenticate with the agent. Commonly, it has to be provided. The address of the target devices is obviously needed. The agent will take care of retrieving the correct data at the desired OID.
What is SNMP walk?
What if you want to retrieve a large amount of metrics via SNMP without having to specify each one? SNMP walk does exactly this. It uses the SNMP GetNext command to retrieve a whole subtree starting from an OID downward. All variables in the subtree below the specified OID are queried and passed back to the SNMP manager.
If no OID is specified, but only the address of a device, all the variables belonging to that device will be polled. This returns a large quantity of data and may be a slow operation.
In SNMP monitoring, this is one of the most useful ways to check the health of a device or a part of your network. An SNMP walk is a simple and easy to automate way to obtain a good view of one or more managed devices.
SNMP traps
SNMP traps are how agents communicate with the manager without being polled. SNMP traps enable an agent to notify a manager of significant events immediately, without waiting to be queried.
The agent has both generic and enterprise-specific types of traps to send. The generic ones are to signal common events like a link being down or up again, the device being reinitialized, or authentication failures. Enterprise-specific traps depend on the vendor and can encompass dozens of different traps.
Whatever type of traps are sent, the manager listens for it and can take action, according to the implemented network monitoring tool. As SNMP traps are the closest to what a real-time notification system is within the protocol, they are of great use in network monitoring for alerting.
What is a community string in SNMP?
SNMP community strings act like passwords to authenticate between SNMP agents and managers. A community string is an alphanumeric string which was notoriously set to “public” by default, but this is no longer common. The string is sent in plain text over the network in SNMP v1 and v2c, and if it matches, access to the agent is granted.
SNMP v3 introduced encryption of community strings, so they are no longer sent in a cleartext over the network, which avoids spoofing. The encryption has to be pre-configured, though. Encrypting SNMP can slow down monitoring as it puts a heavier toll on the agent mainly but also on the manager. So it has to be weighed against the capabilities of the underlying hardware.
Regardless of the SNMP protocol version used, it is strongly advised to change the default community string, as it is well known to attackers. SNMP is not big on security and, unless the network section is closed off from the outside, configuring a custom community string and enabling encryption provide only a moderately secure environment for monitoring.
Monitoring with SNMP
SNMP monitoring is best explained as a combination of agents on managed devices and one or more managers that collect and analyze the data received from the agents. The data that can be retrieved via SNMP is suitable for getting information on the status of devices on the network and is thus ideal for IT monitoring. The monitoring solution acts as a central processor that retrieves data in a targeted manner from the SNMP agents on the monitored devices, or serves as the recipient of event messages.
What are the advantages of SNMP?
The most important point that speaks for the use of SNMP lies in its power to retrieve information from many devices in your network quite easily. Its large adoption within the industry over the years makes implementing an SNMP monitoring solution an easy choice. Many network monitoring systems, like Checkmk, make use of SNMP for collecting information. SNMP is “already there” in most networks, so making use of it in your monitoring often as easy as just activating the agents.
SNMP offers further advantages compared with other network monitoring protocols. It is capable, for example, of retrieving metrics about your cooling, voltage, or temperature sensors. These metrics are not commonly available in other protocols and need a specific agent. Even with the latter, it is not always as easy as with SNMP to get these types of metrics.
Retrieving information via SNMP does not require high-level access rights on the device. A shared community string is sufficient to start exchanging data between the agents and managers. Setting up monitoring via SNMP is therefore simpler than with other solutions.
What problems occur with SNMP?
SNMP monitoring is far from being without problems. Monitoring devices that only send out SNMP traps can cause problems, since they travel as UDP packets, which can get lost. As a result, a problem that has occurred may go undetected.
Even when only using SNMP polling for your monitoring, it is not a foolproof. Network administrators can tell plenty of stories from hell, caused by incorrectly or partially implementing the protocol from devices’ manufacturers. These result in the agent delivering incorrect or faulty data, or the request from the manager timing out. Case-by-case fine-tuning is often necessary by administrators to fix these implementation issues. One solution is using a monitoring tool that already knows which values are incorrect in most cases and can then automatically ignore these, as is the case with Checkmk.
Not all types of information can be delivered through SNMP. For instance, operating system versions or application’ lists on servers are not provided by SNMP, or only to a limited extent. At this point, more agents become necessary to collect this data, not just SNMP ones.
Troubleshooting with SNMP is rarely a quick process. Doing many SNMP walk requests in an environment with numerous hosts often ends up taking hours or timing out. Computing time for some SNMP requests is not the lightest, and it considerably slows down network monitoring with this protocol. An SNMP engine integrated into your monitoring tool, such as it is in the Checkmk Enterprise Edition, can reduce CPU consumption for these requests by up to half.
Some of these problems may seem common to many other monitoring solutions. Yet perhaps they are more severe in SNMP, making some companies and administrators consider it a necessary evil. It has indeed been deprecated by big players in the IT sector like Microsoft and Google, and its future may not be as rosy as it was a few years ago. For the moment though, without a credible alternative to replace it in the near future, SNMP remains an important part of network monitoring.
FAQ
SNMP uses two different ports, the UDP 161 and 162. The first is where the agents listen for incoming requests from SNMP managers, the latter is the port where the manager expects to receive SNMP traps. The source ports in both cases can be any.
Agentless monitoring is a concept in IT monitoring where there is no specific service or software running on the target device to monitor it. This is usually the agent. In agentless monitoring, the remote managing device polls for info on the various devices in a network. These expose their metrics without using an agent at all, but with specific protocols.
SNMP, despite having actual agents installed on the managed devices, is considered an agentless monitoring protocol in practice as the agents are usually already set-up for monitoring. This removes the need of installing and configuring the agent, as in a true agentless solution.
Agent-based monitoring relies on agents being present on the devices to be monitored. These small services take care of collecting the metrics over time and report back to the manager. These agents take part of the load off the managers, which may speed up monitoring in certain cases.
Unlike an agentless solution, agents need to be installed or come pre-installed on each device to be monitored, and possibly configured as well before being of any use.
There are only a few commands of SNMP that are commonly used by network administrators. The most useful ones for monitoring are:
- SNMP get, to request one or more values from a MIB tree.
- SNMP getnext, to request the next OID value in a MIB tree.
- SNMP walk, is a request done on the root node of a MIB subtree to retrieve through a series of get and getnext requests all the nodes in the subtree automatically.
- SNMP bulk walk, is a large request, larger than a walk, to retrieve chunks of OID trees about a network entity.
- SNMP table, is a request similar to walk but outputs the result in a tabular format, easier to visualize.
- SNMP set, is a request to change values on a managed device.
- SNMP traps, is not a request but a notification from an agent to a manager about an occurred event.