Review Checkmk
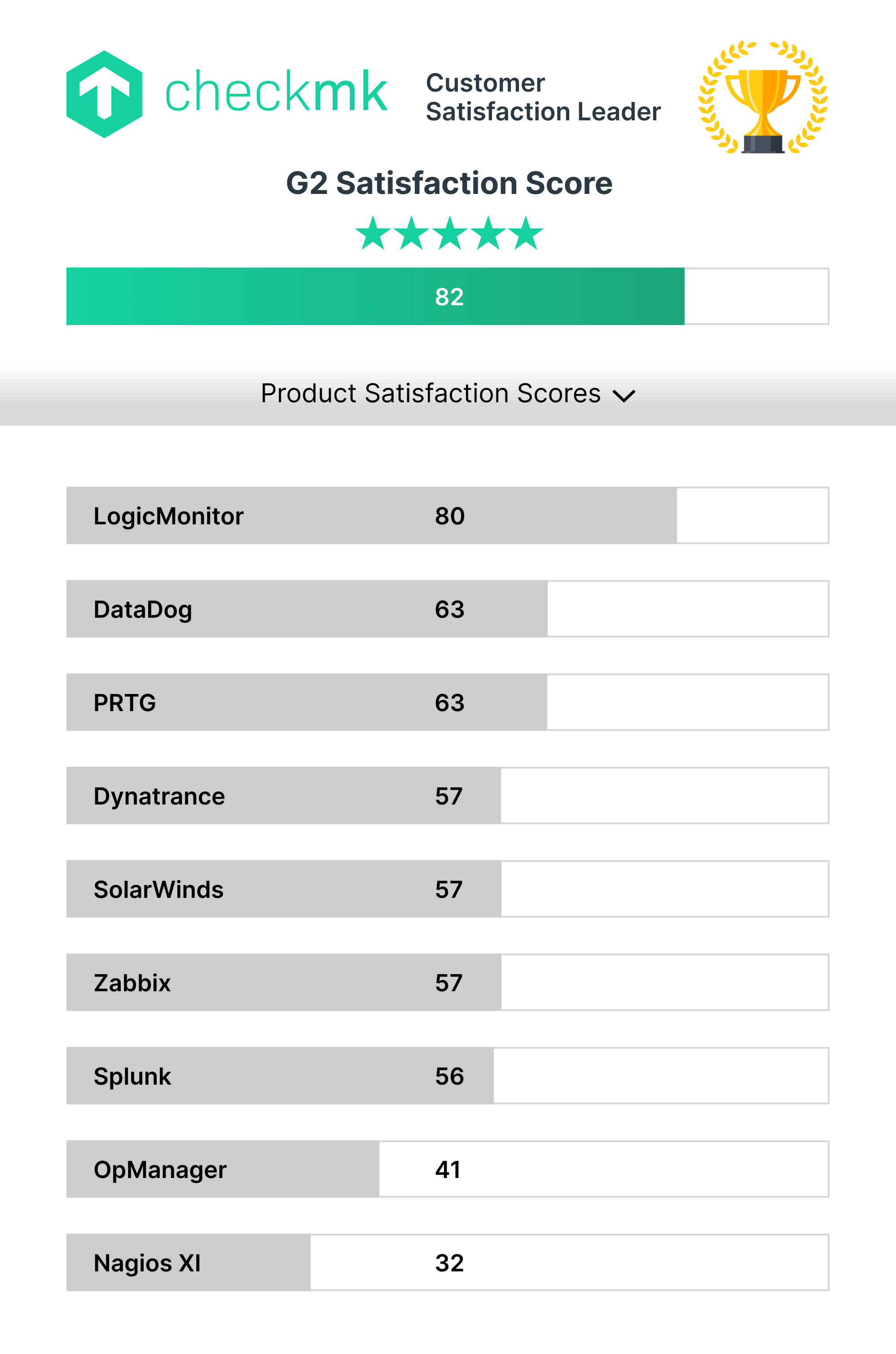
G2 Leader in IT infrastructure monitoring
Discover a state-of-the-art monitoring platform for servers, networks, cloud services, and much more. Find out how Checkmk can solve your monitoring challenges within your hybrid IT infrastructure.
Checkmk is a game-changer for us. Even without prior monitoring experience, it is easy to use.
Marcelo Carvalho - Senior Linux AWS Systems Engineer, ICE Consulting
Scalable, automated and extensible IT monitoring platform
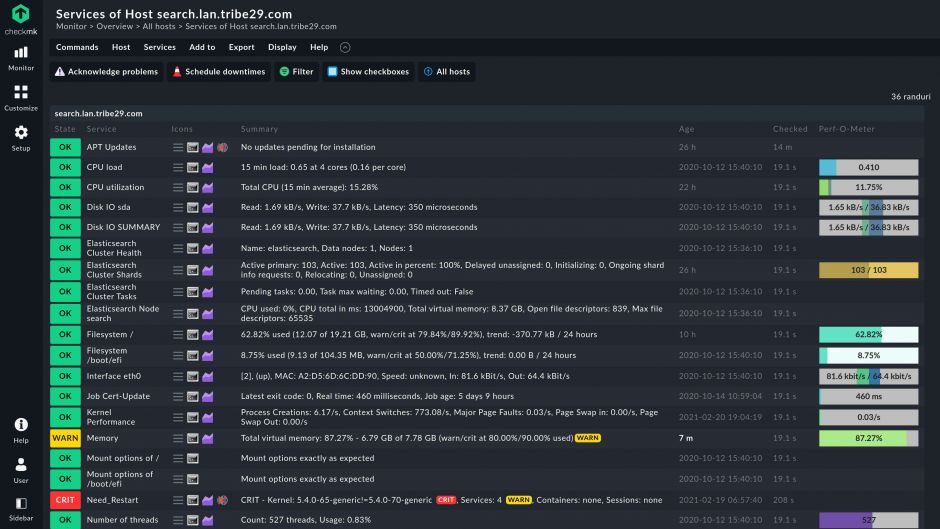
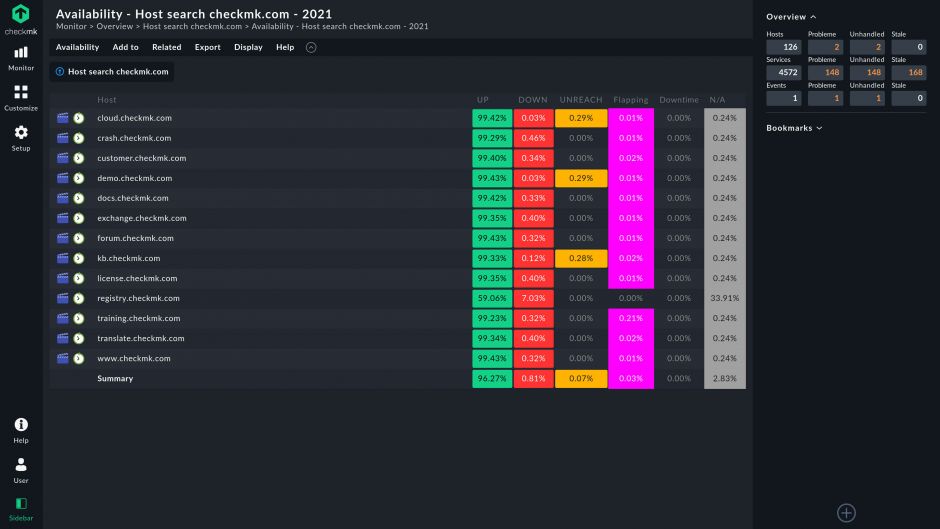
Monitor any workloads
Comprehensive monitoring for every type of infrastructure. Unparalleled coverage of both on-premises and cloud workloads.
- Fast problem identification and root cause analysis
- Multi-cloud ready: AWS, Azure, and GCP
- Support major Kubernetes distros: vanilla Kubernetes, AKS, EKS, and GKE
- Scalable monitoring, distributed architecture
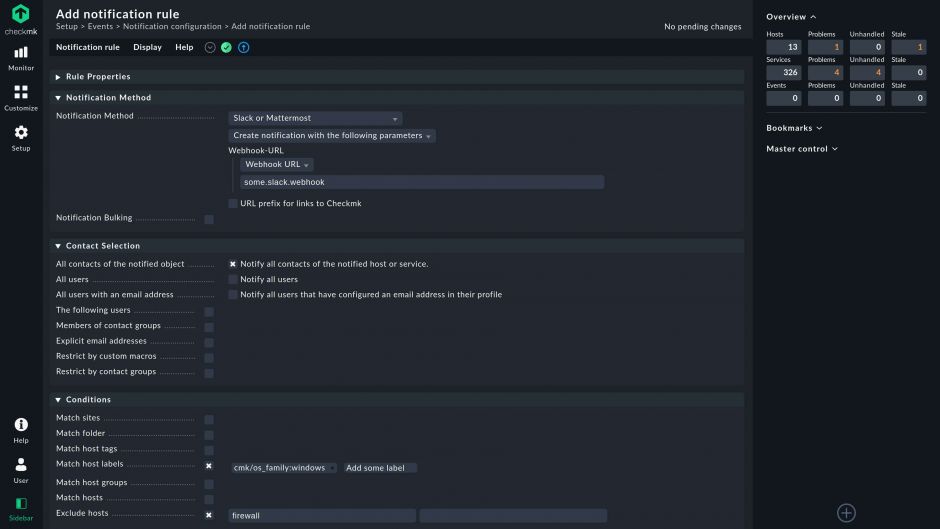
Ready for every operational need
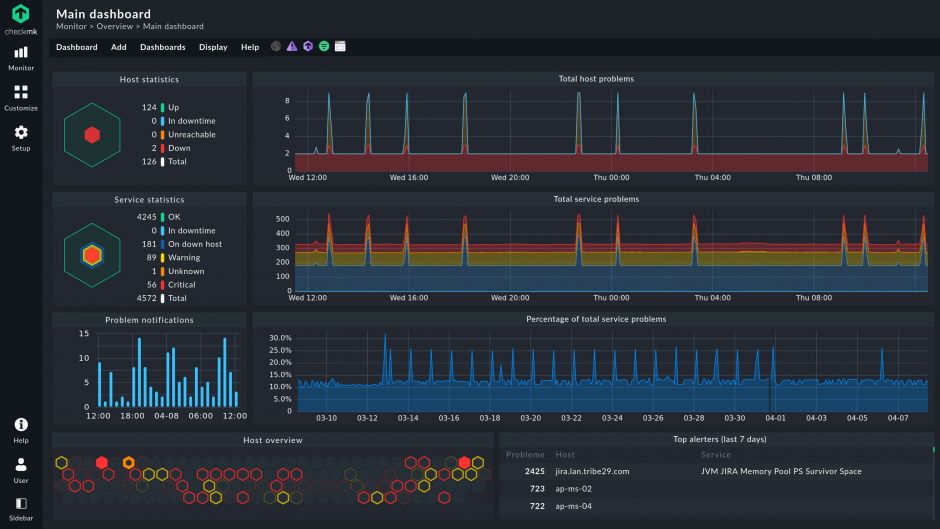
Fully automated monitoring through APIs, auto-discovery, and auto-configuration of plug-ins. Multiple customizable dashboards to check how your infrastructure performs in real-time.
- Agent-based and agentless monitoring in one solution
- Auto-discovery of hosts and services
- Agent management with auto-updates
- Customizable dashboards for modern data visualization
- Advanced filtering capabilities with Tags and Labels
- Powerful, extensive REST API

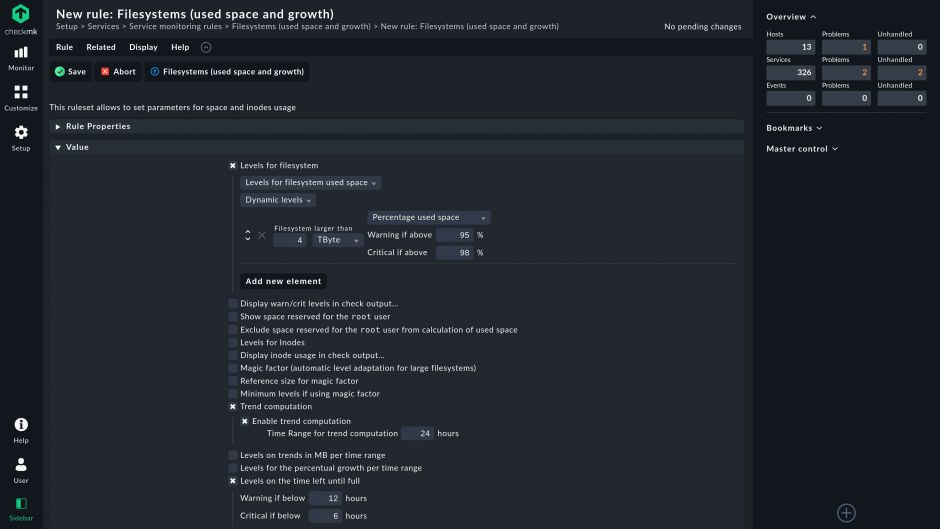
Advanced monitoring features
From zero to monitoring in minutes. Advanced monitoring agents to keep up with the dynamic nature of a modern infrastructure.
- Enterprise-grade security and data protection
- Communication encrypted via TLS
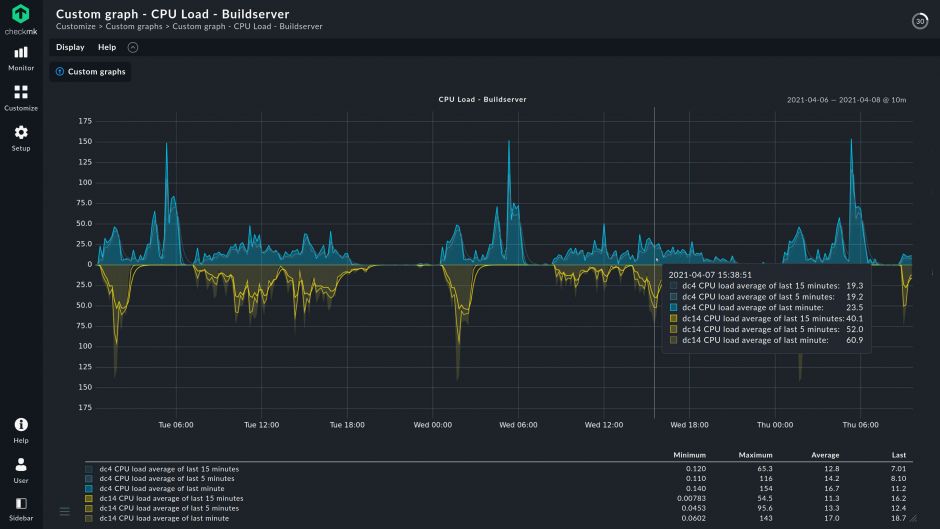
- Advanced analytics for prediction of trends and resource utilization
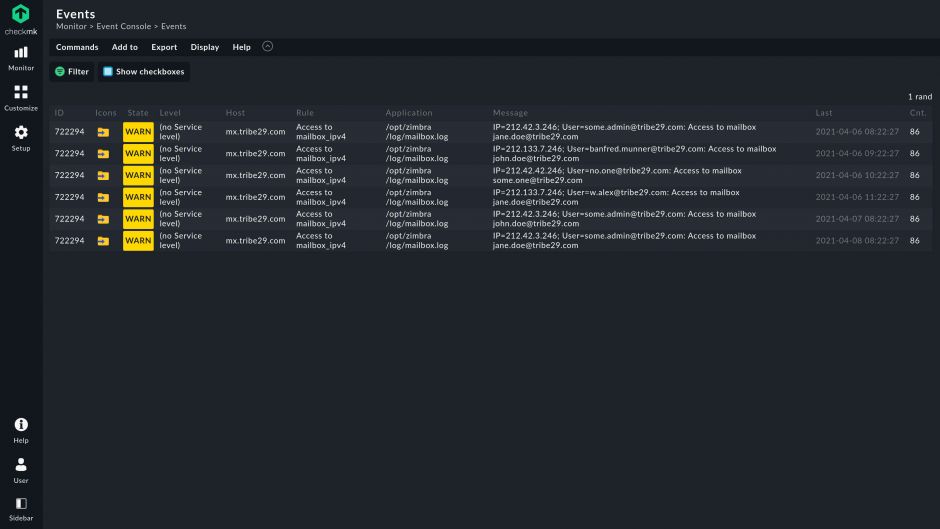
- Smart alerting to reduce notification overload
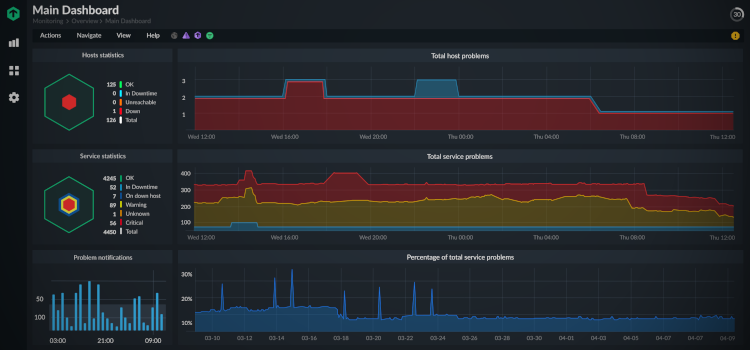
Hybrid IT monitoring platform
Broadest collection of vendor-maintained plug-ins (2,000+) on the market. Highly scalable monitoring solution for hybrid networks.
- Scalable up to hundreds of thousands of hosts
- Extensible plug-in system
- Seamless integration with major ITOM/ITSM tools
- High availability with Checkmk’s virtual and physical appliances
- Designed to be secure: access control via SAML, LDAP/AD, and 2FA
- Smart, granular alerting to reduce notification overload
- Low Total Cost of Ownership (TCO) due to fair pricing, automation efficiencies, small operational footprint, and rapid deployment