Over the past few years, many organizations have had to find a way to share confidential company data with employees in their home offices. This trend in work-from-home arrangements has increased most businesses’ reliance on the confidentiality provided by virtual private networks (VPNs).
Virtual private networks give employees remote access to the company system via the internet through encrypted, virtual tunnels. VPN servers are responsible for managing this network traffic, providing this access for remote users and securing all the data that passes through the system.
The smooth functioning of this system requires the monitoring of all its components, from network devices to software. VPN server monitoring is consequently important for ensuring VPN connectivity, availability and overall system performance.
What are VPN servers?
VPN servers are physical or virtual servers specifically adapted for hosting and providing virtual private network services.
These servers combine hardware and software to determine the encryption mechanisms which ensure that clients' virtual tunnels are properly protected.
How do VPN servers work?
Virtual private network servers check user credentials and data requests from clients, encrypting these communications in virtual tunnels to keep them secure.
Encryption secures the communications of data, thus preventing unwanted parties from easily accessing and seeing the information being exchanged through the tunnels. The encrypted information will be verified by the server and, once authenticated, will be decrypted and sent on to the user requesting the information.
You can set up VPN servers relatively easily as software under almost any server operating system. Operating systems such as Windows come with their own onboard tools for this purpose, but you can also install an additional server application to start a VPN server.
In most cases, however, VPN servers are part of network devices such as firewalls.
Can VPN be monitored?
The short answer to that question is yes, it can. But monitoring VPN is always about more than monitoring a single server service.
It is crucial to continuously monitor the hardware, software, memory, connections, and other components of the virtual network to ensure consistent availability and reliable performance.
The demand placed upon these resources depends on the number and activities of the network clients, so it is essential to track the hardware load on the server host regularly and make adjustments as needed to maintain optimal operation
What is VPN monitoring?
VPN monitoring is the tracking and optimizing of all components of a VPN server.
It involves preparing an inventory of all hardware and software installed in your server and using the appropriate monitoring tools to keep track of their functioning.
With any server, it is standard procedure to observe the CPU, RAM, storage, and network connections. And for a virtualized set-up, standard procedure also includes tracking of the hypervisor and virtual machines and ensuring that the individual VMs are allocated the necessary resources.
This monitoring method also applies to VPN servers. In addition to important metrics such as CPU utilization and main memory utilization, you should keep an eye on the status of the network interfaces.
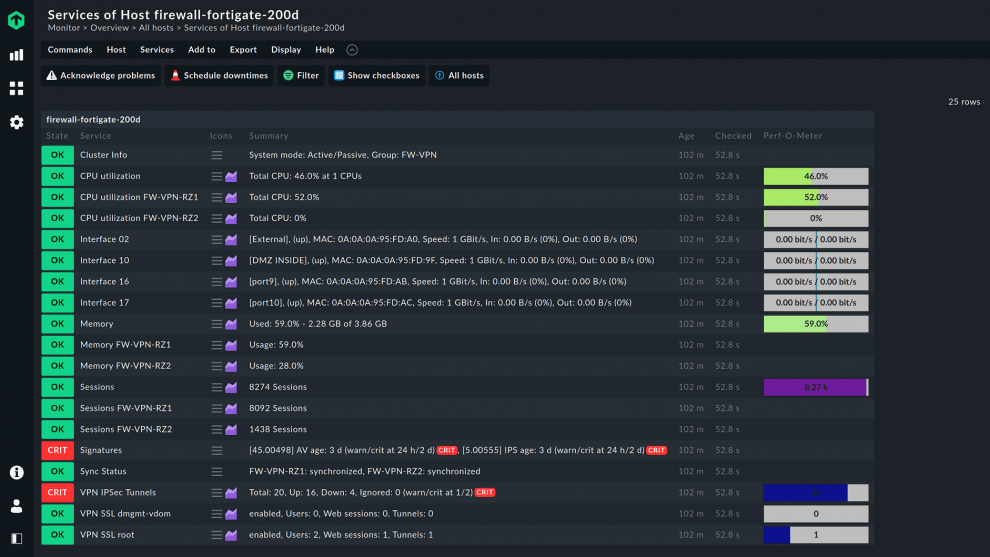
What if a VPN server is part of a firewall?
If a server is part of a firewall, using monitoring agents to keep watch over the server is often not an option because firewall manufacturers do not allow agents to be installed.
However, firewall appliances usually provide monitoring data via SNMP or other interfaces. It is important to keep an eye on the data because the hardware must be sufficiently large.
For this reason, you must include your firewalls when you monitor your VPN server. This is the only way to ensure the optimal operation of your VPN.
Checkmk comes with numerous integrations for monitoring virtual private network servers on network devices such as firewalls.
Among the 2,000 monitoring integrations are plug-ins for these devices from manufacturers such as Aruba, Cisco, Dell, or Linksys, and for firewalls from providers such as Check Point or Palo Alto.
How do I monitor a site-to-site VPN?
A site-to-site virtual private network is often used by larger enterprises to connect their central office with one or more branches.
Tracking internal traffic between these units of a company network must be part of the overall server monitoring process.
Since it is essential that a company’s information remains guarded without disrupting users’ internet speed or browsing experience, monitoring the configuration and network environment in a VPN server is even more critical than for other types of server, both for performance and for data security. You should therefore also consider the users' route via the company’s network to the VPN server. Make sure that you monitor all devices and other components on this route.
Consider individual employees’ and departments’ requirements in terms of VPN capacity, bandwidth, and connectivity. Keep in mind that user devices and internet activity requiring active VPN sessions further impact the server load required for encryption and decryption.
Be aware of the VPN connection’s status and the number of connections allowed by the licensing terms as these, too, affect the server’s capacity to meet user demands.
Network bandwidth fluctuations are also a matter for observation because these result in the underloading or overloading of the VPN servers and user devices.
If the network bandwidth is not sufficient, this slows down the users. Your VPN server may be in the green zone and functioning, but if the network is overloaded, information will be distributed slowly, thereby slowing down all other work processes.
This is why the monitoring of networks is a critical aspect of monitoring VPN servers.
How do I monitor VPN tunnel traffic?
Checkmk makes hosted server monitoring manageable. It has the tools to keep track of not only servers, but also network devices and other assets associated with the hosted environment.
When problems arise related to tunnel traffic in site-to-site VPNs, Checkmk has the tools to spot issues, gather and analyze data on these issues, and address the problems.
If you are monitoring with Checkmk, you can take care of bottlenecks and other potential problems before they become a real issue and maintain high VPN performance.
You can also precisely localize the source of faults and will not be inundated with unnecessary alerts from the monitoring.
Thanks to the many available integrations, setting up and even mapping dependencies in Checkmk is no problem.
And if you provide workstations for your employees via virtual desktop infrastructure (VDI), you can also monitor these with Checkmk. Suitable monitoring integrations for Citrix and other remote workplace solutions are available.