The zero-day exploit Log4Shell endangers numerous servers in companies, being a critical vulnerability in the widely used Java library Log4j. Finding servers with the affected libraries is a priority, so that sysadmins can remediate this threat. Checkmk allows system administrators to easily identify such vulnerable systems in their IT infrastructure and take countermeasures.
With Log4Shell, a new zero-day exploit has become known since last Friday, which puts numerous servers at a critical risk. The exploit allows a flaw in the popular Java library Log4j to be exploited and a shell to be obtained on a server. This allows arbitrary code to be executed on the server and the system to be compromised. The exploit impacts every system running the Java library. That means Log4j affects Windows servers as well as Linux systems.
It is therefore particularly important for system administrators to now be able to identify all systems in their IT infrastructure that use the affected Log4j library. This is the only way to protect the systems from being compromised and to initiate security measures, such as applying security updates. With Checkmk, you are able to automatically identify these systems in your IT infrastructure, regardless if they are running on Linux or Windows.
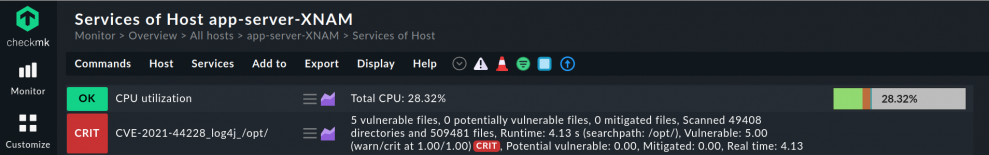
This is possible thanks to Checkmk's rapid extensibility. For example, the monitoring software is able to use a local check to search the file system on a server specifically for the affected Log4j2 modules. The local checks in Checkmk allow you to quickly and easily extend your monitoring. You can distribute these small scripts to the appropriate servers and get for example an overview of all Linux and Windows servers where Log4j2 libraries are installed.
Update from December 20th:
In the meantime the Checkmk Community worked on and created a sophisticated plugin that you can install as an extension package to your monitoring. The plugin helps you to detect all systems in your IT infrastructure which are affected by the Log4j exploit. All information about the plugin can be found below.
Update from January 27th:
We also created a video about the plugin and how it helps you to detect vulnerable files on your systems. There, Mathias and Robin also show how to configure the plugin in your Checkmk site:
Vulnerability scanner and mitigation patch for Log4j2
Updated on December, 16th 2020 at 01:00pm (CET)
The Checkmk Community reacted very fast to the exploit and shared their first scripts for Checkmk to detect Log4j2 vulnerabilities in their IT infrastructure. Forum user Doc used log4j2-scan to write a shell script for CVE-2021-44228 vulnerability scanning and mitigation patching for Linux servers:
#!/bin/bash
# Christian Wirtz, 2021-12-15
# Wrapper around:
# https://github.com/logpresso/CVE-2021-44228-Scanner
# for checkmk usage - used Logpresso CVE-2021-44228 Vulnerability Scanner 1.6.2
# https://github.com/logpresso/CVE-2021-44228-Scanner/releases/download/v1.6.2/logpresso-log4j2-scan-1.6.2-linux.tar.gz
# extract this into ../../bin/
DESTPATH="/usr/"
COUNT=0
RESULT=`/usr/lib/check_mk_agent/bin/log4j2-scan $DESTPATH`
FILES_VUL=`echo "$RESULT" | grep "vulnerable files" | grep -v "potentially vulnerable files" | awk '{ print $2 }'`
FILES_POTVUL=`echo "$RESULT" | grep "potentially vulnerable files" | awk '{ print $2 }'`
FILES_MIT=`echo "$RESULT" | grep "mitigated files" | awk '{ print $2 }'`
SCANNED=`echo "$RESULT" | grep "Scanned"`
RUNTIME=`echo "$RESULT" | grep "Completed in" | awk '{ print $3 }'`
SHORT="$FILES_VUL vulnerable files, $FILES_POTVUL potentially vulnerable files, $FILES_MIT mitigated files, $SCANNED, Runtime: $RUNTIME s"
LONG=`echo "$RESULT" | awk 1 ORS='\\\\n'`
PERFDATA="vulnerable=$FILES_VUL;1;1|potential_vulnerable=$FILES_POTVUL;1;1|mitigated=$FILES_MIT;;|real_time=${RUNTIME};;;1;"
echo "P CVE-2021-44228_log4j_$DESTPATH $PERFDATA $SHORT (searchpath: $DESTPATH)\n$LONG"You might want to adjust the DESTPATH depending on how broad you want to search. Please keep in mind to place the script and log4j2-scan bin (tested with v1.6.2) in the right folder of the agent of the host and make them executable. The structure under /usr/lib/check_mk_agent/ should be:
|-- bin
| `-- log4j2-scan
`-- local
`-- 86400
`-- check_CVE-2021-44228_log4j.sh
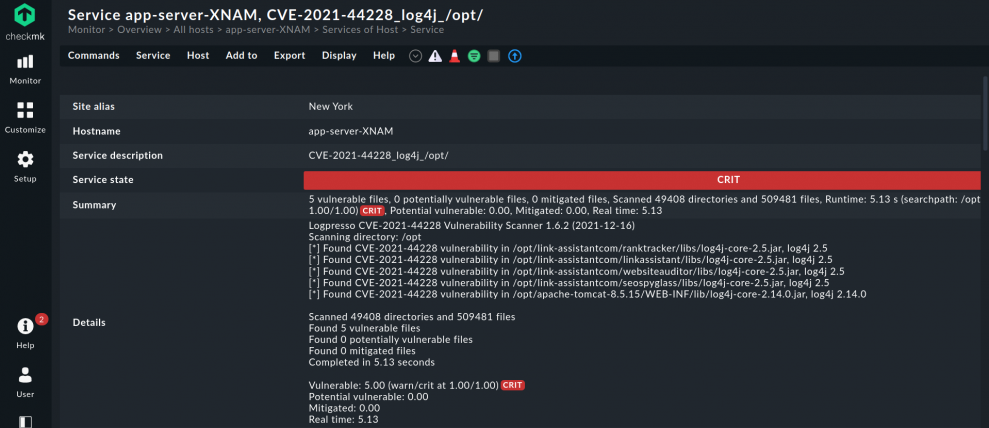
You can easily install CVE-2021-44228_log4j by using it as local check. Be aware to insert the current version of the binaries log4j-scan AND log4j2-scan.exe in the right folder. The binaries can be found on the GitHub repo of Logpresso.
If you want to identify vulnerable Windows systems you can also easily do this with a local check. With both scripts, Checkmk can help you to quickly track down all systems that are vulnerable to the Log4Shell exploit.
Local check to detect Log4j2 on Windows servers
Based on the work of Doc, thl-cmk, adopted the Windows script for the latest version of log4j2-scan.exe (v.1.6.2)
<#
thl-cmk@outlok.com, 2021-12-15
Wrapper around: https://github.com/logpresso/CVE-2021-44228-Scanner
for checkmk usage based on the bash script by Christian Wirtz
#>
$RESULT=(C:\ProgramData\checkmk\agent\bin\log4j2-scan.exe --all-drives)
$FILES_VUL=((echo $RESULT | Select-String -Pattern "vulnerable files" | Select-String -Pattern "potentially vulnerable files" -NotMatch | Select-String -Pattern "Fixed" -NotMatch) -split ' ')[1]
$FILES_POTVUL=((echo $RESULT | Select-String -Pattern "potentially vulnerable files") -split ' ')[1]
$FILES_MIT=((echo $RESULT | Select-String -Pattern "mitigated files") -split ' ')[1]
$SCANNED=(echo $RESULT | Select-String -Pattern "Scanned" | Select-String -Pattern "Running scan" -NotMatch)
$RUNTIME=((echo $RESULT | Select-String -Pattern "Completed in" ) -split ' ')[2]
$DRIVES_SCANNED=((echo $RESULT | Select-String -Pattern "Scanning drives" ) -split ' ')[2]
$SHORT="Files: $FILES_VUL vulnerable, $FILES_POTVUL potentially vulnerable, $FILES_MIT mitigated, $SCANNED, Runtime: $RUNTIME s, drives: $DRIVES_SCANNED"
$PERFDATA="vulnerable=$FILES_VUL;1;1|potential_vulnerable=$FILES_POTVUL;1;1|mitigated=$FILES_MIT;;|real_time=${RUNTIME};;;1;"
$LONG=$RESULT -join "\n"
# if someone needs the count metric uncomment the next line (count and vulnerable metric are identical)
#$PERFDATA="count=$FILES_VUL;1;1|vulnerable=$FILES_VUL;1;1|potential_vulnerable=$FILES_POTVUL;1;1|mitigated=$FILES_MIT;;|real_time=${RUNTIME};;;1;"
echo "P CVE-2021-44228_log4j $PERFDATA $SHORT\n$LONG"The local check for Windows platforms needs to be placed in the directory %ProgramData%\checkmk\agent\local\ on the target host. The binary for the script log4j2-scan.exe must be downloaded from GitHub and inserted in the directory %ProgramData%\checkmk\agent\bin\. Now the check should work and you can detect Log4j on Windows servers in your infrastructure.
Fast response to Log4Shell exploit
In the Checkmk Community the Spanish user a3093 was one of the first members, who shared such a script for Checkmk to track down the Log4j2 libraries in the IT infrastructure in our forum. If you are interested into the conversation check out the topic in our forum. The script scans all systems for potentially affected .jar files.
A detailed guide on how to roll out local checks on your systems to detect Log4j2 modules on Windows servers or Linux systems can be read in detail in our documentation.
Checkmk plugin scans for vulnerable Log4j systems
Updated on December, 21th 2021 at 7 pm (CET)
Due to the excellent spirit in the Checkmk community, a sophisticated plugin for Checkmk has been created in the meantime from Doc's script by thl_cmk, which not only rolls out the CVE-2021-44228-Scanner of Logpresso (version 2.3.1 for Linux and Windows from 12/19/2021), but also takes into account the different outputs the tool delivers from newer versions on. In this way, it is possible to detect vulnerable Log4j libraries on Windows and Linux systems in your infrastructure and to customize the time series data for the service in Checkmk.
The plugin discovers the following Log4j issues:
- CVE-2021-44228
- CVE-2021-4104 that affects also Log4j1 libraries
- CVE-2021-42550
- CVE-2021-45105
- CVE-2021-45046
You can download the plugin as MKP here. After downloading it can be rolled out on the target system(s) for Checkmk Enterprise Edition users via the Agent Bakery. Attention: Before you use the package please remove all older versions or the local checks related to this plugin.
If you want to use the plugin with the Checkmk Raw Edition, please follow these instructions from thl_cmk. It also covers the deployment on AIX/Solaris systems and provides some help for troubleshooting in case the plugin does not work.
Having such a flexible method available in Checkmk comes in handy often, especially when dealing with vulnerabilities.
