Deeper insight into your network monitoring
In network monitoring, most software relies on classic SNMP to furnish the data. When the protocol is well implemented, it can provide a good deal of info about network utilization and the status of the devices on the system. In most cases this can be plenty. Yet administrators may require a more in-depth analysis of their networks and SNMP may be limiting for their needs. Especially when trends and patterns of the traffic are desired, SNMP shows its limits.
In these cases, network flow monitoring software is necessary. A network flow is a set of meta information derived from the data traffic. A flow records a series of information that focuses on who is talking with whom, using what protocol, using which port, and the amount of bandwidth used for these exchanges of data. It is of great help in identifying bottlenecks in your network. Instead of having to monitor single devices and connect the dots yourself, you have a view of all the flows that happen across the network, and immediately know where the greatest amount of packets go to and from. Using one of the many flow monitoring tools, the administrators are able to know who is doing what, when, and where on the network, and how the traffic data flows in their infrastructure.
Network flow monitoring also includes packet inspection. The network flow data sets are very tightly consolidated, but such packet insights require access to the raw packets – which can only be obtained via a mirror port or a Network Tap. However, these can usually also be connected as a data source for a network flow analysis.
The flow protocol family
The flow data is provided via a family of protocols such as NetFlow, sFlow, IPFIX, and many others. Cisco was the originator of this family, born with the intention of simplifying the creation of access lists. The collected data proved to be useful for much more than that, and NetFlow was released. Many producers besides Cisco support this family of protocols with their own, like J-flow from Juniper Networks, NetStream from Huawei, and Rflow from Ericsson. The most recent and most used protocol in the family is IPFIX, based on version 9 of NetFlow and supported by the IETF (Internet Engineering Task Force).
How a network flow works
A flow packet contains various types of meta-information: typically the IP address of the sender and the receiver, the source and destination ports, Layer 3 protocol types, the classification of the service, and the router or switch interface. The protocol groups all packets with the same contents into a flow and then summarizes the packets and bytes together at the end.
Network components that support a network flow protocol create and send such a flow packet via a push method. An exporter software is tasked with collecting and transmitting these flow packets, acting as an agent. A collector is assumed to exist on the network, which is typically the role a network flow monitoring tool assumes. The collector gathers the data records. Depending on which protocols it supports, this collector converts these data into standardized values, thus preparing them for examination. The collector then forwards the data to a central instance, which then displays the processed data graphically, making it available in the form of a GUI for quicker insights. Flow monitoring tools are intended to be both the collector and the central console, both being necessary for network traffic flow monitoring.

Extend network monitoring possibilities with flow monitoring
Flow-based monitoring tools therefore help you to have a clearer, broader image of what your traffic is like. Flow packets contain info that tells an administrator where traffic is coming from, over what protocol and port, and where it is going to. This is what network traffic flow monitoring is. There are multiple advantages of using network flow monitoring on your infrastructure.
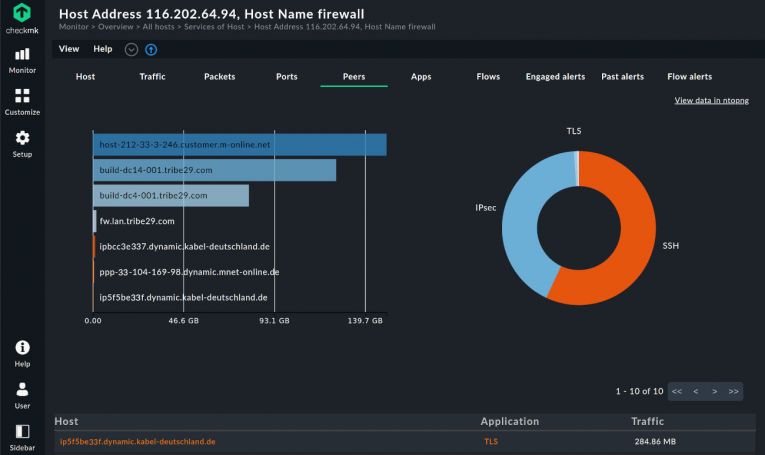
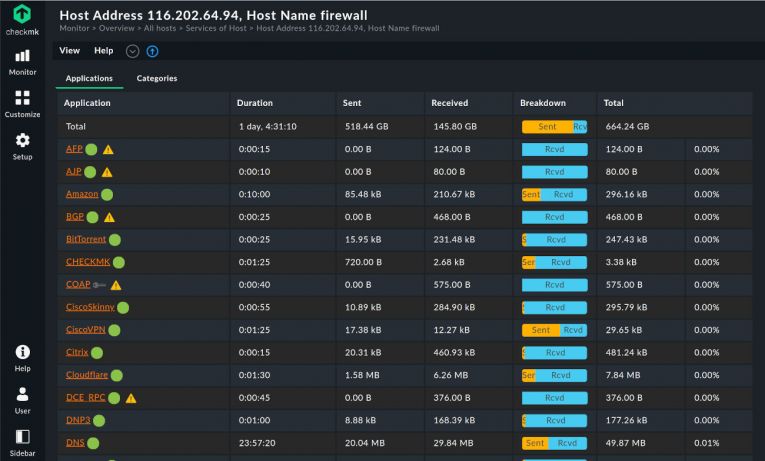
Network flow data provides detailed information on network hosts such as traffic, packets, ports, peers, and applications. These allow for easier detection of anomalies and malfunctions in your network. Some examples of use cases include detecting when DNS is misused, when invalid certificates are implemented, or when the TLS encryption does not work correctly. Network flow monitoring software can provide all this info.
Network security monitoring is an area where network flow monitoring software can help as well. Analyzing the network flows on your network can help you recognize unusual patterns – and dangerous ones in particular. Ransomware traffic can be identified, just like any type of intrusive exchange of data that normally shouldn't happen.
Flow monitoring tools can give you an interesting view of the top talkers and listeners on your network. They can break down usage by source, destination address, protocol, or application. This is especially useful in capacity planning, to inform the administrators of when and where the network is reaching capacity and why.
Detecting the causes of spikes in bandwidth usage is easier with a network flow monitoring tool. One of its main purposes is to precisely monitor the usage of the network, bandwidth included. Merged with a dashboard, as is the case with Checkmk, this provides an immediate view of how your network is performing and how it is being used.
Ultimately, network flow monitoring is helpful in many ways, not least in implementing an efficient Quality of Service (QoS) on your network, prioritizing business-critical applications, and ensuring no disruptions occur.

Why then use a network flow monitoring tool?
Considering the possibilities offered by network flow protocols, it is clear how adding a further layer of metrics and views to your network monitoring is advantageous. Network flow monitoring does not have to be in contrast with SNMP monitoring but rather enhance it, adding more info to have an as holistic as possible view of your infrastructure. Most network devices come with support for both SNMP and network-based flow monitoring, making the choice a non-issue.
A network flow monitoring software solution can provide more information than one that limits itself to SNMP or other classic network monitoring protocols. And when talking about monitoring, the more info you can access, the more chances to identify possible issues and problematic patterns. Most flow monitoring tools are not specific to network flow monitoring but integrate it, as does Checkmk. It is not always necessary to have separate software running to monitor your network flow traffic packets along with SNMP traps or analyzing logs from many different hosts. One network flow monitoring-enabled software solution is sufficient for all these tasks in the case of Checkmk, greatly simplifying your infrastructure.
Implementing network flow monitoring software is therefore a relatively easy and hassle-free way to increase the efficiency of your network monitoring. Tools like Checkmk include a vast range of protocols and plug-ins to cover all your monitoring needs. There is hardly a reason not to use a network flow monitoring tool.

FAQ
Is NetFlow still used?
Yes, NetFlow is still used and commonly found on many routers, switches, bridges, and other network devices. Officially it has been superseded by IPFIX, but support for the original protocol is still widespread.
What are the protocols of the network flow family?
The network flow family of protocols is vast. NetFlow is the most well known, but after and, nowadays, along with it, many others exist, created by other vendors. Currently part of the family are Argus, Jflow, NetStream, Cflowd, Rflow, AppFlow, sFlow, and IPFIX.
Ready to explore the full feature set of Checkmk?
Download the free trial and see it in action.