What is VPN monitoring?
VPNs are largely used in today’s corporate world. Their features and efficiency are the backbone on which many employees work and the infrastructure of their companies use. But an inefficient VPN means sluggish connections and difficulties in accomplishing work-related tasks. Their promise of security is vital for many companies. VPN needs to be monitored too, same as any other component of an IT’s infrastructure, since there is no guarantee that a VPN will work at all times.
VPN monitoring is here to ensure that every VPN is as efficient as it should be, and that the data is only seen by authorized eyes. VPN monitoring is done either through specific software or via the generic monitoring solutions that plenty of companies implement for their network monitoring strategy.
VPN monitoring examines the health of all related VPN devices that constitute the private networks, and monitors VPN traffic, making sure all the data moves through the VPN network without delay, and all information is encrypted. Additionally, VPN monitoring can report on each user’s traffic bandwidth usage and notify about spikes or abnormalities. Resources can then be allocated when and where needed. VPN monitoring does not only help administrators have a good performing enterprise network, but also inform them on how to maintain and optimize it.
TL;DR:
VPN monitoring ensures secure, efficient, and reliable connections for users and networks by tracking the integrity, traffic, and performance of VPNs.
- It checks VPN tunnels, devices, and gateways to ensure traffic is encrypted, connections stay active, and values such as latency, packet loss, and bandwidth usage remain within acceptable limits.
- Remote-access VPNs connect individual users to a network, while site-to-site VPNs link multiple networks together.
- MPLS-based VPNs use cloud infrastructures for interconnecting locations — monitoring for these is often handled directly by the provider.
What is actually a VPN?
A VPN is, as the acronym suggests, a virtual private network. In practice, it means one of two things. A VPN can extend a private network across a public network, enabling its users to send and receive traffic as if it were one single private network. It can also allow individual users who are not necessarily connected to a private corporate network to connect to one remotely, and have the same permissions and access as if they were physically connected to the other hosts on the network. Therefore, a VPN is not only a method to merge different networks, but to also add a specific host to a remote network.
Regardless of whether they are networks or individual users, a VPN connects several of them through the use of tunneling protocols that take care of encapsulating the local traffic and transferring it over a public network. The traffic is encrypted at the origin and decrypted at the destination, making it safer from third-parties and sniffers. Through the use of VPN tunnels, confidentiality, efficiency, and full features are ensured across different private networks.
To make a secure connection in a VPN possible, an ad-hoc protocol is used. There are a few that can create the necessary tunnels in a VPN, authenticate users, encrypt the traffic, and maintain high efficiency. The most common ones are IPSec, SSH, and OpenVPN. These allow workers to communicate across different networks with adequate security, performance, and transparency, which is the main use case for a VPN.
The different types of VPNs
Different types of VPNs have different use cases. The main ones are to connect an individual user or a group to a private network, or to interconnect multiple private networks. The former is called “remote-access VPN” while the latter is known as “site-to-site VPN”. In the consumer world, mostly remote-access VPNs are used, the business world focuses on both.
These categorize VPNs according to their use. Other ways to classify a VPN are also according to the tunneling protocol used, the level of security provided, the OSI layer they present to the connecting network, and the number of simultaneous connections. These are rather technical classifications, which have different implications in the practice of the companies. We will focus exclusively on the remote-access and site-to-site VPNs instead.
Remote-access VPNs
Remote-access VPNs permit a user to connect to a private network and access all its services as if they were on a local network. The connection occurs through the internet, and perhaps through more than one private network, depending on how the infrastructure is set up.
Companies implementing remote working make large use of remote-access VPNs to allow their employees to access internal resources without them being physically close. Monitoring a VPN like this is thus vital for companies to provide remote workers an efficient network for their job-related tasks, to combat abuse, and to identify intrusions.
Consumers make use of remote-access VPNs to increase their privacy when browsing the internet and allowing them to access region-restricted content. This type of VPN is the most commercialized and more commonly paid for by end-users. It is also the easiest to set up, as commonly only a client software is necessary to connect to the VPN provider or, in the case of an employer's VPN, the private network. A few data like IP address and personal credentials are generally all that is necessary for a user or employee to join a VPN.

Site-to-Site VPNs
Site-to-Site VPNs are also known as Router-to-Router VPNs. Effectively, they connect one router to another router, as their scope is to join two or more remote private networks as if they were one. Companies use this type of VPN to connect locally-different networks to one another, sharing resources across multiple networks. For instance, their central office with a series of branches. Technically, they bridge a router to a router, hence the alternative name router-to-router VPN.
Depending on what is connected, the VPN is further differentiated in Intranet based and Extranet based VPNs. The former is when a VPN is used to connect several networks of the same company, while the latter is used when different companies join their networks.
MPLS-based VPNs
A subcategory of site-to-site VPNs are MPLS-based VPNs. They work in all regards as normal VPNs, but instead of relying on the hardware of a single company, they are cloud-based VPNs. A third party takes care of setting up the VPN and connecting your private networks with each other, ensuring stability and confidentiality. The MPLS network functions as the tunnel by which a company creates virtual connections between office sites. Traffic therefore goes through this cloud-based network, where the VPN monitoring takes place.
The main advantage of this solution is speed. As they are dedicated businesses, MPLS-based VPNs are generally very efficient. VPN monitoring is usually done by the companies offering this VPN solution, thus outsourcing the needs of a VPN monitor altogether. Furthermore, MPLS-based VPNs offer interface independence, meaning that each of your networks can have different types of connection and still work together as a VPN. Their main downside is that it is a paid solution with an increased weight on the company's budget.

VPN tunnel monitoring
At the core of a VPN, there are its tunnels. VPN tunnel monitoring is thus also the core of VPN monitoring. Most of VPN monitoring is about VPN tunnel monitoring and only marginally about checking VPN status.
There are multiple network protocols that act as tunneling protocols. Any VPN tunnel monitoring is therefore done with a monitoring tool that can support the protocol used in your organization, or directly checks the traffic at gateway level. Most commonly these are either IPSec, SSL/TLS, SSH, L2TP, and OpenVPN, with a few alternatives that are OS-specific or rarely used.
Why is VPN monitoring essential?
As with any type of network monitoring, checking the health of your VPN is essential to have an efficient network. VPNs are increasingly used for remote working and connecting different networks, often very far away from each other. Both are critical aspects of operating a modern company. Monitoring the VPN is important to understand how well it is working, improve its performances whenever necessary and, in the end, guarantee an optimal experience to everybody who is using it. VPNs can be the principal way to how employees connect to the company’s network, and ensuring that they suffer no disruption and slowness is fundamental for them to perform their tasks as well as they can.
A VPN is an effective way to maintain a good level of security when transferring sensitive data, as the VPN tunnels are encrypted end-to-end. In network security monitoring, it is important to include VPN monitoring, and checking that the traffic is actually encrypted. Keeping track of who is connecting to a VPN is a good method to know who is authorized and who is not. Unknown attempts of connection can signal attempts of intrusion. Old accounts of former employees that have not been disabled yet may still access internal resources, and a VPN monitor is necessary to discover them before a security emergency arises.
What to monitor in a VPN?
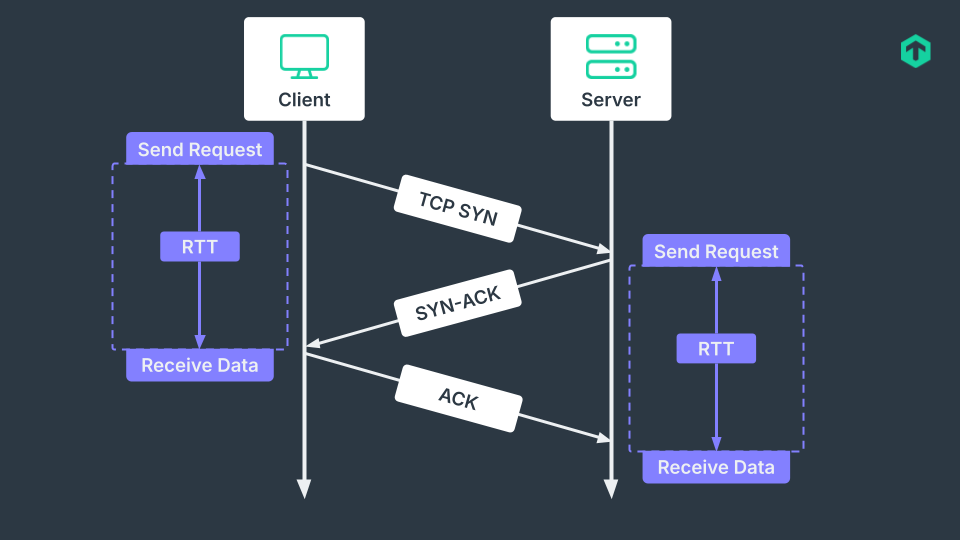
Whether your infrastructure has a site-to-site VPN or a remote-access one, there are a number of key metrics to monitor that are common for both. Checking the VPN status, if it is up or down, is the most basic check to make in VPN monitoring. Metrics that focus on the health of the VPN are the next logical step. Round-trip time (RTT) is a measure of how long in milliseconds it takes for a request to go from a starting point to the destination and back again. In VPN monitoring, this is often checked by collecting the average and the maximum RTT of both public and private networks. RTT will give you insight on how efficient the VPN is.
Packet loss rate is the natural metric to collect to identify congestions or overworked network devices. Along with the actual traffic being used, where it goes and where it comes from, this can give the network administrator a good view of why there may be a large packet loss rate at a particular point in the VPN.
Naturally, knowing the overall bandwidth usage is important for being aware of what is being used and by whom. Usage spikes may signal an anomaly or intrusion. This is usually collected on a VPN gateway that monitors all traffic coming and going in a VPN.
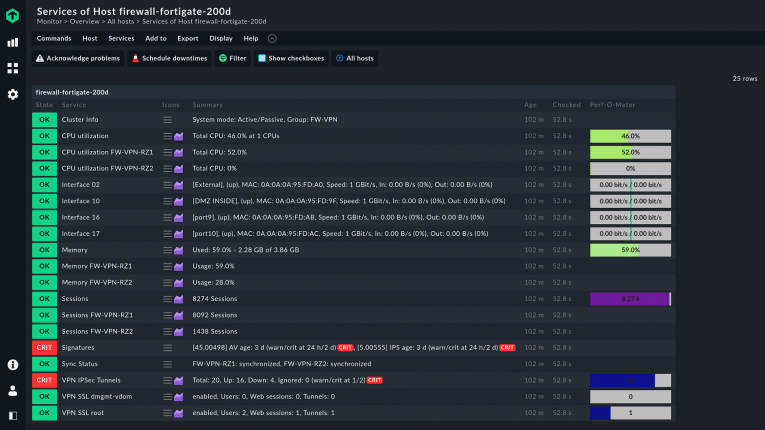
The total number of VPN sessions and tunnels is indicative of how many active users are connected through the VPN. Any number that deviates from the norm may indicate an intrusion or a security misconfiguration.
How VPN monitoring works
In practice, VPN monitoring is done with the help of a network monitoring solution that can handle monitoring of the various devices through which VPN traffic is routed. This includes routers, gateways, switches and dedicated VPN servers. Everything that goes from a network to another via VPN, plus anything under the control of the company in the case of remote-access VPNs, needs to be monitored. This is a large amount of data to check, especially if we consider that the traffic in a VPN is encrypted and then decrypted, with further burden put on the CPUs.
Therefore, all the metrics that can interest a VPN connection are to be collected. VPN traffic monitoring is a key part of VPN monitoring, with bandwidth, number of open VPN sessions, number of active VPN tunnels, error rates, and packet loss contributing to the general view of how a VPN is performing. It also checks the CPU utilization of each VPN device. Most network monitoring tools include these metrics by default.
Once the basic VPN status is checked, and all the useful data about VPN traffic is captured, real-time monitoring in order to set usage threshold is commonly set up. In many cases, but not always, VPNs have to impose limits to not be abused. A real-time VPN monitoring system can apply threshold by user, network and/or tunnel.
VPN monitoring solutions present all the collected data with a visual dashboard and with data reports. While the dashboard is usually used to check the health of the VPN on a daily basis, in-depth reports can help you to identify possible issues and bottlenecks better. Some monitoring tools allow for an automated response to events with preset and custom rules. Leveraging rules to respond quickly to issues and alerts means a reduced manual intervention with fewer possible human mistakes and less workload for administrators. Checkmk does support all these features for an easy VPN monitoring solution that does not skimp on metrics.
FAQ
What is a VPN used for?
In a business setting, a VPN is used to allow remote users to securely connect to an internal private network or to join multiple internal networks as if they were one. This permits a sharing of internal resources as if they were all on the same network. In a consumer setting, VPNs are offered to provide increased security, to access region-restricted content, and to overcome government’s censorship.
What is VPN logging?
VPN logging is the act of collecting logs about the activity on a VPN. These logs may include user-specific and privacy-sensitive data like visited URLs, usage metadata, DNS requests, and browsing history. In VPN monitoring, connection logs are analyzed instead. These include bandwidth usage, dates and time of each connection, origin and destination IP addresses, and VPN server IP address.
How to check VPN status?
There are various ways on how to check VPN status, all dependent on the type and setup of your VPN. They go from the most basic, a ping to one of the private network addresses, to the most user-friendly ones, a custom dashboard coming with the chosen VPN service. VPN monitoring tools can of course set alerts and notify you when any changes in the VPN status occur.