What is a firewall?
A firewall is a line of defense for any network or device. Usually the very first. The firewall monitors incoming and outgoing traffic, and controls what can be transmitted and what is blocked according to predetermined security rules. Firewalls are a critical component of a network, helping to safeguard the entire infrastructure that is behind them. A firewall is typically used to establish a barrier between a trusted and an untrusted network, but its scope can be much larger, encompassing blocking unauthorized accesses to an environment or controlling internet access for a specific set of applications from a series of terminals. The most common example of a firewall is to prevent unauthorized access from the internet, but there are plenty of other applications for a firewall.
Firewalls are split into software and hardware types. Both control traffic, but the software ones use the resources of the host they are installed on, while hardware firewalls have their own dedicated resources. This is the main distinction between the types of firewalls, beyond which they are categorized by how they operate.
A packet filter firewall inspects the packets transferred between computers and allows or blocks them according to preset rules. Stateful firewalls can also keep track of the state of network connections, such as TCP streams, UDP datagrams, and ICMP messages. These can act over a whole connection, not just packet by packet. Further up are application firewalls, which operate on an application-level, being able to distinguish applications from one another, and allow or block traffic to or from these. Deep packet inspection firewalls are advanced packet filtering systems, capable of inspecting the actual content of each packet and filtering these if desired.
Regardless of the technology behind a firewall, all are rules-based. Rule standards can be applied to large and small items, for example to all of the incoming packets down to a particular type of packet trying to access a single device, on a specific port. The granular control provided by most firewalls is quite high. Keeping track of how a firewall operates is the central point of what monitoring a firewall is all about.
TL;DR:
A firewall is a network security barrier that controls incoming and outgoing traffic based on predefined rules, protecting devices and networks from unauthorized access.
- Firewalls can be software or hardware, and range from basic packet filters to deep packet inspection systems that operate at the application level.
- Monitoring a firewall ensures rules remain up-to-date, detects misconfigurations, and identifies unusual or unauthorized traffic in real time.
- Logs and metrics on traffic, port usage, and rule compliance provide insights to maintain security, enforce policies, and optimize performance.
What is firewall monitoring?
Firewall monitoring, as can be imagined, is done with a firewall monitoring software. This may be a standalone tool but in practice it is common to have a network monitoring tool that can check the status of firewalls alongside a plethora of checks on other parts of the infrastructure. These tools also monitor firewall traffic to identify unusual patterns or unauthorized access attempts. Firewalls aren’t particularly complex to monitor and therefore the task of monitoring a firewall is only one of the many that a monitoring solution can accomplish.
In truth, firewalls are victims of the misconception that once set up, no monitoring is necessary. As with any other piece of your network, anything that is not monitored may later cause undetected issues. Firewalls are no exception to this. Therefore, the monitoring of firewalls has to be part of a good network monitoring system. As we will shortly see, there are a number of good reasons for monitoring a firewall.
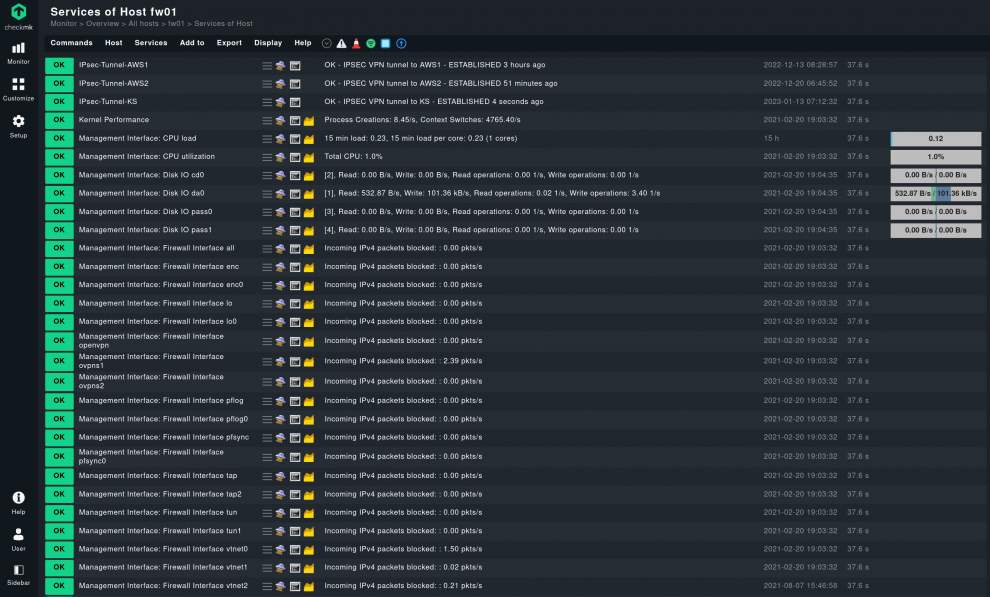
Why is a firewall monitor important?
The effectiveness of a firewall greatly depends on how up-to-date its rules are. If a new application is installed without a respective rule to control its traffic, when necessary, then the application may not work at all, as its traffic is blocked by default. Whenever a new host is connected the firewall rules may need to be updated to include or exclude it, depending on its role in the network. A new user will have a new set of applications and services that they will need access to, and a firewall may block it.
It is clear then that the first reason why a firewall monitor is important is to avoid potential problems that can be caused by a set of outdated rules. By monitoring your firewall this can be checked and identified. Rules can then be modified as required to reflect the changes in the infrastructure without causing any service disruption. In addition, tracking firewall rule changes through detailed monitoring and audit trails helps also maintain security and compliance, by highlighting outdated rules that can cause vulnerabilities exploitable by malicious parties.
A second factor for the importance of monitoring a firewall is the limiting of human error. A large percentage of data leaks are due to inadvertent mistakes by employees. Mistakes cannot be 100% eliminated, clearly, but they can be detected by monitoring. The ways with which hackers steal credentials include the typical malware and phishing tricks, both of which generate traffic. A firewall monitor can detect this traffic as it happens, and notify in real time about potential security incidents.
Lastly, having clear firewall policies help in keeping the rule set optimal. Still, if it is not monitored, it is hard to know for sure if these policies are being correctly applied. Here firewall monitoring plays the role of a watcher, checking that the rules are active, and that all ports have the correct status.
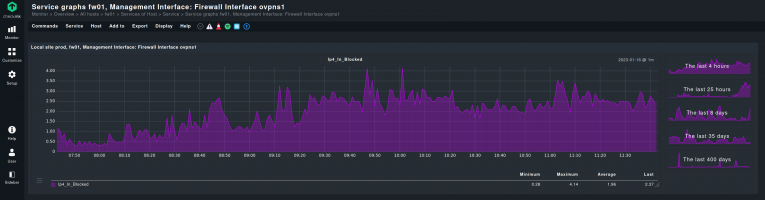
Firewall logs: the foundation of monitoring
Firewall logs are at the heart of effective firewall monitoring, providing a comprehensive record of all network traffic passing through your network firewall. Reviewing event logs is a critical part of firewall monitoring, as it helps detect anomalies, supports security audits, and ensures effective policy enforcement. These logs capture essential details such as source and destination IP addresses, ports, protocols, and the specific action taken by the firewall, whether traffic was allowed or blocked. By analyzing firewall logs, organizations gain critical insights into firewall activity, enabling security teams to monitor network traffic, track changes to firewall rules, and ensure that firewall configurations align with security policies.
What to check when monitoring a firewall
Monitoring a firewall is mostly concerned with the monitoring of a firewall’s rules. The core of a firewall lies in its rules, and the primary task is to ensure that these rules do not conflict with business processes or with each other. Regular monitoring helps identify misconfigurations that could expose the network to risk. Rules should not override each other, as this causes all sorts of random behaviors that are hard to monitor later. Firewall monitoring software is capable of checking rules as soon as they are implemented.
Not only should rules not be in conflict with other rules, but rules that are no longer required should also not be kept. This can be a security risk, mainly because it can result in ports from a very old rule being left open, a situation that may not have been detected by administrators. Without proper firewall monitoring, such detection is not an easy task. Checking that all rules are actually being correctly applied and that they are required by the policies in use is an important task for the firewall monitoring service.
Firewall log monitoring is the practice of monitoring the logs generated by the firewalls. These provide plenty of insight on how the firewall is performing, what is being blocked, and if any rules are not being triggered. Log analysis also plays a crucial role in identifying vulnerabilities within the firewall setup. As well as the usefulness of catching outdated rules, perusing the logs can be informative in various other situations.
For instance, knowing which rules are being most often triggered can not only inform the administrators of the traffic trends, and their changes, but enable them to detect many unusual behaviors. A firewall port that was never used and which suddenly becomes very active, can be grounds for treating this new traffic as suspicious. Similarly, ‘false positives’ can also be found in the firewall logs. These are sources of traffic that interact with the firewall, but should not.
Firewall log monitoring is supported by the vast majority of firewall monitoring systems. And, if it is not supported, it is good practice to check the logs manually.
Which metrics are relevant in monitoring firewalls?
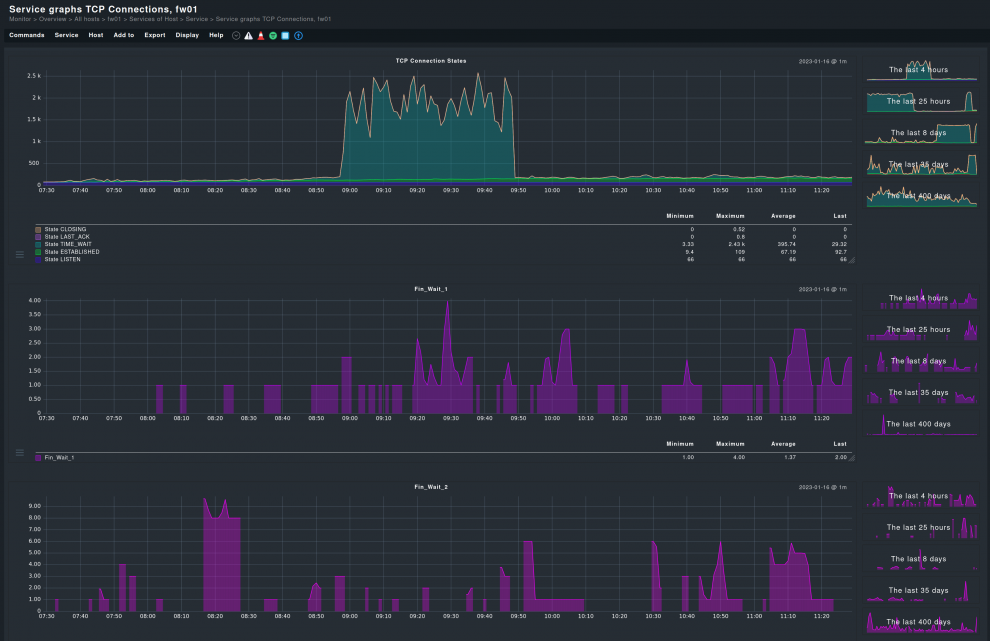
Firewall monitoring tools are not only about rule-checking, but also about collecting a series of metrics that help administrators understand how the firewall is performing. These metrics typically fall into three main categories: traffic and performance, network activity (such as ports and connections), and rule compliance.
1. Traffic and performance metrics
Traffic and network performance metrics cover parameters such as bandwidth usage, throughput, latency, number of active sessions, and resource utilization (CPU and memory) — all of which help illustrate how traffic is managed as part of firewall monitors’ tasks. Monitoring these indicators and incorporating them into comprehensive reporting provides insight into the firewall’s capacity and efficiency, enabling administrators to detect bottlenecks, strengthen security, and ensure the resilience of the overall network infrastructure.
2. Network and port activity
Network and port activity metrics reveal how connections are established and controlled. This includes monitoring which ports and protocols are in use, verifying whether the ports align with firewall rules, mapping active sessions to their respective rules, and identifying unexpected or blocked traffic. Such data helps administrators detect misconfigurations, enforce security policies, and adjust firewall rules when necessary.
Ports are especially relevant, as they lie at the core of firewall rules and serve as a key metric for determining whether a rule is being applied. By “ports” we mean not only TCP/UDP ports, but also the physical ports on a hardware firewall. This activity complements port monitoring, which focuses solely on ports.
3. Rule and compliance metrics
Rule and compliance metrics track the state and changes of firewall rules. Monitoring firewall rules through a firewall monitoring service ensures that modifications are documented, unauthorized changes are flagged, and compliance with internal policies or external regulations is maintained. This visibility enables administrators to quickly trace who made a change, why it was applied, and whether it aligns with organizational standards.
Best practices for monitoring firewalls
Firewalls are not all the same. Different firewall technologies are implemented in various firewalls under all the operating systems. Linux firewall monitoring does not function in the same way as Windows firewall monitoring. Thus, make sure that you are monitoring the firewalls according to how they work. A generic check of ports and what traffic goes through them is insufficient. It is important to delve into the differences between Linux and Windows firewall monitoring when considering a firewall monitoring implementation. This topic goes beyond the scope of this article, but it is important to mention as a best practice for monitoring firewalls.
Regardless of whether a Linux or Windows-based firewall is in use, the firewall software needs to be up-to-date. Your monitoring tool of choice should be capable of signaling an outdated version. To prevent any risks and ensure that your firewall is working to its full potential, make sure that its software is regularly updated. Proactive monitoring and regular updates help prevent vulnerabilities before they can be exploited.
Firewall monitoring is not a process that simply runs continuously, one that once implemented and started can be forgotten about.
It is important to conduct regular firewall security audits. These are designed to check whether the firewall rules are in accordance with the company’s security policies and compliance requirements. This is made easier with a proper firewall monitoring, but in any case it needs to be done from time to time.
Firewall monitoring can detect when a new or changed rule is opening unwanted ports somewhere in your network, but the consequences of this are yours to decide. Instead of applying rule changes in production, it is a better practice to do so in a staging/testing environment. Monitor the firewall there too, before committing the changes to production. Even a few minutes of an untested firewall rule may mean too large a security risk for most companies to accept.
How to choose a firewall monitoring tool?
Choosing the right firewall monitoring software is primarily a matter of the available support. Firewalls are both hardware and software, and a tool for monitoring them definitely needs to support the actual ones you have in your network. Hardware firewalls are specific devices that may or may not be supported by most firewall monitoring tools. If not, make sure that you can monitor them through SNMP, as a last resort.
When selecting a firewall monitoring tool, the primary goal is to maintain robust network security through effective monitoring. Comprehensive network security relies on continuous oversight, policy enforcement, and rapid response to threats, all of which are enabled by choosing the right monitoring solution.
Software firewalls mean those coming with Linux, other Unix-like operating systems or Windows. Windows firewall monitoring has its own requirements, which differ from those of Linux or Solaris or AIX. There are even multiple types of firewalls under these systems, and a good firewall monitoring tool needs to be able to monitor all of them. Windows firewall monitoring means at least monitoring the Windows Defender Firewall, which is supplied with Windows itself. Many proprietary and open-source alternatives exist, with their own ways of setting rules and blocking traffic.
Virtual machine monitoring implies checking for their firewalls too. In most environments there are virtual machines, serving a range of purposes, and these are of course integrated into the network they run in. Monitoring a virtual machine firewall is therefore an important weapon to have in your arsenal.
Similarly, cloud services have their own networks and relative cloud firewalls. These are a vital part of modern infrastructures, and logically need to be monitored by your firewall monitoring tool of choice.
An important feature that does not improve the actual monitoring but which makes the lives of administrators easier, is a visual interface to be able to immediately see the status of your firewalls. This is best provided with a dedicated dashboard to check each firewall, and thus to be able to see at a glance if anything is amiss or wrong, basically. Detailed firewall log monitoring and firewall rules monitoring need to be integrated into the monitoring dashboard so that they can be operated with ease.
FAQ
What is firewall log monitoring?
Firewall log monitoring means more than just checking the logs produced by a firewall. Both software and hardware firewalls generate logs that contain valuable insights into how the firewall is functioning. Analyzing these logs is crucial not only for understanding firewall performance but also for identifying vulnerabilities, detecting security threats, and spotting misconfigurations that could expose the network to risk. With continuous monitoring, security teams can quickly detect unauthorized traffic, unusual patterns, or attempts to exploit outdated rules. This immediate visibility helps prevent breaches and ensures the network remains secure against both internal and external threats.
What is Nagios firewall monitoring?
Nagios firewall monitoring is the monitoring of a firewall using Nagios, the network monitoring application which Checkmk was originally based on. With Nagios it is possible to monitor both software (such as the Windows firewall) and hardware firewalls.
What is Cisco firewall monitoring?
Cisco firewall monitoring refers to the checking of the status and collecting metrics from the popular series of Cisco firewalls, such as Cisco ASA. Monitoring these through SNMP is always an option, but firewall monitoring software also does so through the use of custom tools, like in Checkmk with its cisco_asa_connections plug-in for example.