Port monitoring: What it is, why it matters, and how it works
Keeping an eye on ports is essential for effective network monitoring. Find out what ports are and what you must take into account when performing port monitoring.
TL;DR:
A port in a network is a physical or virtual connection that allows devices to communicate, and monitoring these ports ensures network reliability and performance.
- Monitoring ports helps detect failures, bottlenecks, misconfigurations, and hardware issues, providing a clear view of network health.
- Key metrics include bandwidth usage, packet loss, and port status, which enpower troubleshooting and capacity planning.
- Port monitoring improves security by revealing unauthorized connections and allows better network topology mapping.
What is a port?
The most basic definition of a port in a network is dual. A port can either be physical or virtual. Today, we will focus on the former, but a short definition of both is necessary before continuing.
A physical port is one of the many connectors that computers, and hardware in general, use to link different devices. In networking, a network port transmits data across devices, using one of the many existing network protocols. These ports are found on most computers, and on any server, switches, routers, modems and similar network devices. Physical network ports come in many shapes, but the most commonly used in network and telephony contexts are the RJ11, RJ25, and RJ45 (RJ stands for “registered jack”).
Unlike physical ports, virtual network ports do not take actual space on a device, but are logical ports. They are a terminology used by network protocols to open a communication channel between a source and a destination, separating them by their port numbers.
Virtual ports’ signals travel through the physical ones. They are not exclusively wired, since connections can be opened wirelessly. This is why, in the context of port monitoring, we focus on the physical ports, where a physical cable can be connected to. These include unidirectional ports, in which the flux of data goes in one direction only, like uplink and downlink ports, or access ports, to which users can directly attach their terminals.
All these can, and should, be monitored with a port monitoring solution, for reasons that we will explain to you shortly.
What is port monitoring?
A network only works if all its components do. If one or more is faulty, the consequences are not only felt by your network administrators, but by the users too. Switches and routers are at the core of the network, and each of their ports is vital to make it flawlessly work. Once communication is interrupted between even two of them, serious problems may arise.
What port monitoring is about is checking the status and overall health of a port in a network to prevent failures, identify bottlenecks, make an inventory of ports and relative devices, and be promptly alerted of any changes. Port monitoring is a subset of the larger network monitoring. It is sometimes called network port monitoring as well, even if it is a redundant term.
Port monitoring includes the more specific switch port monitoring, firewall monitoring, router port monitoring, and is done with a network monitoring software with port monitoring functionalities, like Checkmk has.
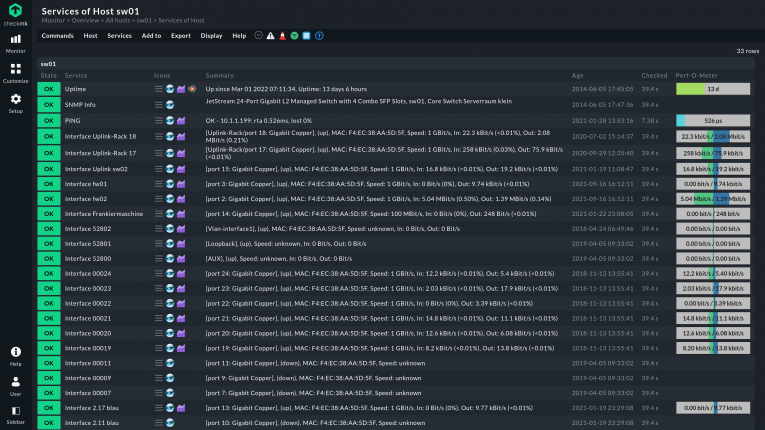
What metrics of a port can I monitor?
A few metrics help detect possible issues that affect your ports. The used bandwidth of each port, for example, can tell you which port is more active, which is underused, and which ones are unnecessary or need to be checked for hardware failures.
Changes, especially sudden ones, in the throughput may be a signal of problems. Such changes need to be monitored on a port level, rather than on a whole node, to be the most accurate.
With appropriate monitoring software, it is also possible to monitor the packet loss rate at each port. A high rate can be a sign of various issues like a failing or loose cable, or a malfunctioning port. Multiple ports on the same device showing similar high packet loss rates may indicate the device as the cause instead. But to know for sure, all ports have to be monitored.
The status of a port, active, inactive or down, is an important metric to monitor. Other than being the base metric to know if a particular port works at all, it may signal more serious issues worth investigating. Failing or disconnected ports will reflect their changed status in Checkmk and generate an alert.
Most of these metrics have to be interpreted, not all are clearly showing the “why” of what a port monitoring scans reports. Nonetheless, they are important factors to take into consideration when analyzing the poor performance or any type of issues related to your network. Each of these metrics contribute to a holistic view of monitoring, making port monitoring another stepping stone to a healthy and performing infrastructure.
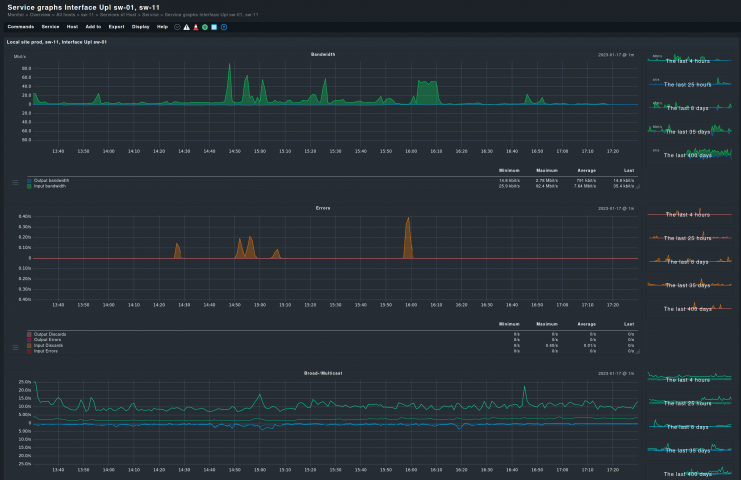
Why is port monitoring important?
Port monitoring adds a second layer to your monitoring. It does not substitute monitoring your CPU usage, hardware sensors, or services monitoring but gives further insight into them. Discovering a network device being overused is important, but adding the gained knowledge that its ports are under constant and heavy traffic can also tell you the why.
You may be having a shaky connection on a particular switch, but unless you monitor all its ports, you won’t know if the whole device or one of the ports is the cause. By monitoring all your network interfaces, it is possible to detect broken patches or installation cables, which are other common causes of network outages and disconnections.
Worst of all, a single port being inadvertently disconnected or failing can cause major outages. While most ports are not that vital for an infrastructure, a few certainly are. Port monitoring is necessary for administrators to avoid these types of outages.
There are not just physical-related issues to be discovered with port monitoring. Logical and software related issues are also possible. Auto-negotiation of network interfaces’ capabilities like speed and duplex mode are common, but not completely reliable. Misconfiguration can happen, causing one device to try to operate at lower speed than possible, slowing down an otherwise functioning port’s traffic.
A port with a high rate of packet loss may be a sign of duplex mismatches. These happen when directly connected network interfaces are misconfigured, with one operating in half and the other in full duplex mode. Similarly, protocol drop issues happen when a data transmission protocol is implemented, but the router does not recognize it. Knowing how each port behaves can bring to light these misconfiguration issues.
A port performing poorly may not have anything to do with the port itself or the device it is mounted on. It may be a damaged or faulty cable instead. These can cause corruption of the transferred packets and even bring the physical interface in the switch to go down and up, intermittently. Issues like port flapping and similar synchronization problems can be identified with an adequate port monitoring setup.
Port monitoring merges with other types of monitoring to provide a holistic view of your infrastructure. Not monitoring your ports means accepting a partial view instead, far from the objectives of proper network monitoring.
What are the benefits of port monitoring?
Besides the obvious advantages discussed so far that a port monitoring software can offer, there are a few further perks of port monitoring. They are, however, not necessarily correlated with ports misbehaving and catching possible issues on your network.
Modern port monitoring software can create an advanced network topology through port monitoring. By analyzing each port, checking their IP addresses and subnets, a complete image of the network is made. This not only includes the various networks, but also how they are interconnected. This is the base for live network monitoring.
Having metrics like used bandwidth, packet and error rates on each port on your network gives you the knowledge of what is more utilized and what is not. Capacity planning becomes clearer through network port monitoring. There won’t be any doubts whether it is an old router or increased traffic on it that causes slowness, nor will resources be wasted in replacing still functioning devices.
Furthermore, by monitoring ports, you can recognize unauthorized physical connections to switches and/or routers. A rogue user can connect with a terminal to your network and without port monitoring you would not know. With Checkmk, it is easy to notice if a supposedly inactive port suddenly becomes active, generating traffic. Without switch port monitoring, this would go unnoticed.
And it goes the other way too. By knowing your unused ports, you can block them and increase the network's overall security.
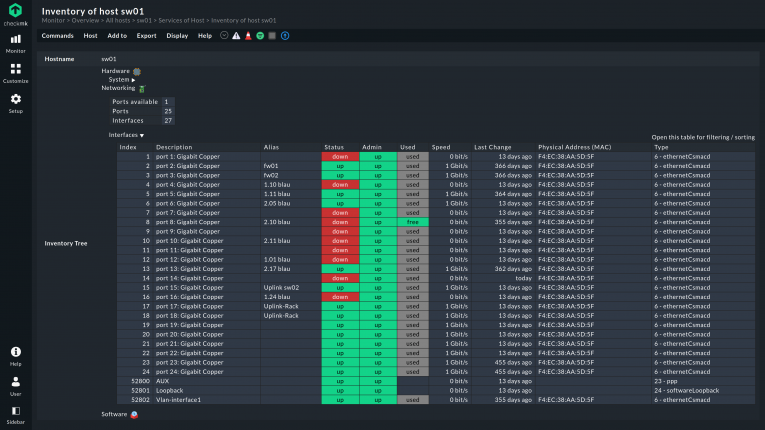
What are the challenges of port monitoring?
Port monitoring comes with its challenges. First is the risk of “alert fatigue”: misconfigured port monitoring can quickly lead to a flood of false alarms when any port can trigger notifications. For example, this could be access ports triggering alerts when a device is powered on or off, even though this is a common occurrence. Having to find the important alarms in such a large volume of false alarms is not only very time-consuming, it can also quickly tire out the IT team responsible. The configuration of your monitoring tool of choice is therefore necessary to reduce these unimportant alerts and make port monitoring an efficient part of your monitoring efforts.
Similarly, when setting up port monitoring, you have to pay attention to what ports are included. Usually an initial port scan is done to discover all the ports present on a network. That only catches the ports that are active at a given moment, not those offline. A normal port scan is therefore not sufficient, but an advanced one, like Checkmk does, can also include the offline ports in the monitoring. As soon as they become active again, they will normally be monitored like any of the others.
FAQ
What is TCP port monitoring?
TCP port monitoring operates on virtual ports only. Unlike physical ones, TCP or UDP ports are practically infinite, with new ports becoming active or going inactive every moment. Whereas physical ports are finite, rarely changing in numbers, virtual ones present a highly dynamic landscape.
Monitoring TCP ports is connected with monitoring single applications or services, and firewall monitoring, rather than switch and router monitoring. Administrators use TCP port monitoring to know what ports are active on every device, if any traffic is wrongly blocked by a firewall, if applications are using a TCP port that they should not and so on. Checkmk does both physical and TCP port monitoring.
What is a TCP port?
A TCP port is a logical construct that identifies a process or network service with a number. In the TCP protocol, ports are used to identify specific services, and are completed by an IP address. The combination of source address and port, together with the destination address and port, constitute a complete channel of communication across devices.
What is port mirroring?
Port mirroring is the process of sending all the traffic that comes through a physical port on a switch to another port, located on a connected device. It effectively mirrors every packet and sends it to a remote device for analyzing.
This way a specific port can be monitored on a device set up for the task, like one running a packet analyzer, or a network stress testing tool, which will replay the traffic over parts of the network to test for performance bottlenecks.