What is a switch?
A network switch is a device that connects other devices together in a computer network. Here we are specifically discussing computer networks, but of course there are switches in other fields too. All operate in similar ways, by connecting different devices through their physical ports. Most computer network switches fall into one of two categories, data link layer and multilayer switches. The former use the MAC addresses of devices to direct traffic to the appropriate destination, while the latter can also use IP addresses.
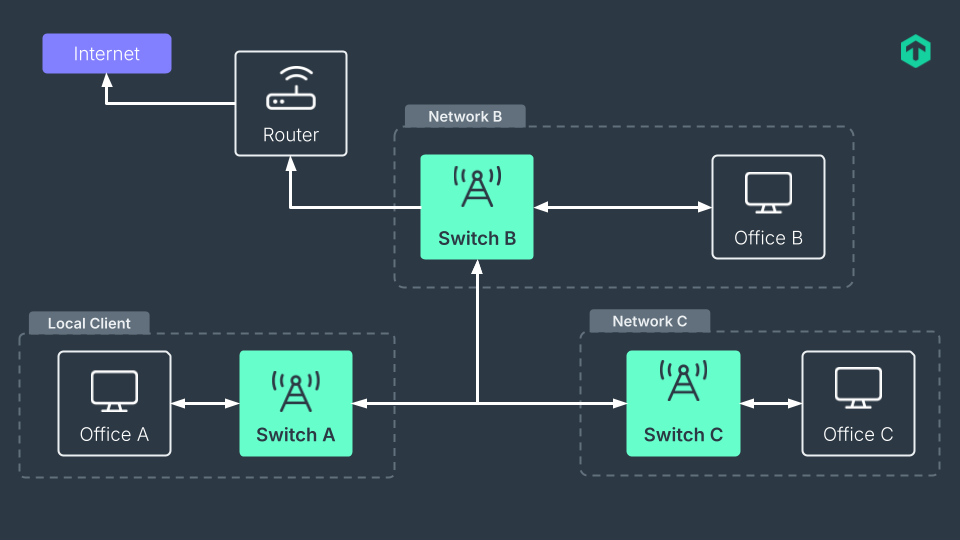
Functionally, they do the same job: ensuring that a packet from a source reaches the right destination. This role must not be confined to a single network as switches can also connect multiple networks.
Switches are fundamental components of modern networks, serving as the backbone of both performance and reliability. They manage communication between multiple devices within a local area network, ensuring efficient data transfer and organization. It’s only natural, then, to implement a switch monitoring system to safeguard the network’s overall stability.
What is a switch port?
Switch ports are physical connections to which devices can be attached, and which connect to the network the switch operates on. In the vast majority of enterprise networks, these ports are Ethernet ones, the most common also in consumer-grade devices. Switches have multiple switch ports, on a variable number that goes from fewer than a dozen to multiples of ten. When more ports are needed, more switches can be added and possibly interconnected.
These ports are the ones monitored when implementing port monitoring — a subcategory of switch monitoring focused on assessing the performance of individual ports rather than just the switches themselves. Monitoring switch ports is essential for effective network management, as it involves continuously tracking port status and detecting unusual activity through automated alerts. Since all network traffic passes through switch ports, they are a critical element that cannot be overlooked when monitoring your infrastructure.
What are the types of switch ports?
There are many types of switch port, differing in the supported network technologies, network architecture’s role, and functionalities. Ethernet switches will have RJ45 connectors, while Token Ring switches have STP connectors. The family of SFP connectors is to be found on switches that support Gigabit Ethernet or Fibre Channel networks. Similarly, for other network technologies, switch ports will be physically different. Switches supporting more than one type of connector are common though.
Depending on the switch port’s role, we have access, trunk, and hybrid ports. Access ports give devices access to a single network, while trunk ports connect different networks. Hybrid ports play both roles. These roles are independent of a switch port’s physical form.
Furthermore, there are a few special types of switch ports with specific functionalities. A stack port is one used to connect other switches of the same model, brand, and switch software version. These are useful to increase the port capacity of a network as all the thus stacked switches will have a usable port number equal to the sum of the combined switches. PoE (Power over Ethernet) switch ports are capable of carrying data and power on a single port, saving physical space on the rear of switch hardware.
All of these various ports can be regularly checked in network port monitoring, with their collected metrics of course differing according to the ports’ roles and network technology. Monitoring tools can also be configured to focus on only critical ports, which is an industry best practice for efficient switch management.
TL;DR:
Switch monitoring continuously tracks all devices and ports in a network to maintain stability, performance, and security.
- Monitoring must include both the switches themselves and their ports, tracking status, bandwidth, packet flow, and errors to detect malfunctions or misconfigurations.
- Combining SNMP, flow protocols, and modern interfaces provides a complete view of network traffic and device health without overloading IT teams.
- Continuous monitoring enables proactive capacity planning, prevents service interruptions, and strengthens security by identifying unused or unauthorized ports.
What is switch monitoring?
Switch monitoring is, simply, monitoring all of the switches in a network. ‘All’ being an important word here since only by having a holistic view of the network is it possible to be aware of every issue, disruption, and misconfiguration. Switches are key components in any infrastructure, making network switch monitoring an indispensable tool in your overall network monitoring.
The term, monitoring a switch, has a number of meanings. As switches are separate devices, with their own processes, switch software versions, hardware, and capabilities, they need to be monitored as you would any other host. Switch monitoring is then not only a way to monitor the traffic but also includes the actual checking of how each switch in a network is performing. Both what/how data flows through a switch and the device itself make up a switch monitoring.
Monitoring connected devices and their connection points helps maintain network health, optimize performance, and prevent potential disruptions. By continuously monitoring your switches, you can effectively take the pulse of your network — understanding how well each switch is performing and receiving timely alerts in case of any malfunctions.
Switch monitoring with Checkmk of course allows you to monitor both the devices and the network traffic, as well as supporting port monitoring to also have switch ports under control. It is important to not exclude either component when implementing a switch monitoring solution.
How to monitor a switch
The king of switch monitoring is still SNMP. Through this protocol, widely supported by switch vendors, it is relatively easy to monitor all of your switches. SNMP can be used directly from a terminal, but these days user-friendly interfaces which include integrated SNMP commands have been implemented by many network monitoring tools.
Many switches do not however allow the installation of third-party agents supplied with modern switch monitoring software, so limiting the monitoring possibilities to SNMP. This does not mean that SNMP is the only way to monitor a switch. Network flow monitoring protocols such as NetFlow and sFlow are well-supported by switches, including those that forbid the installation of external agents. These protocols focus more on the sources and destinations of traffic going through the switches, which is clearly useful but not a complete view of how a switch is working. A mix of SNMP and a flow monitoring protocol, wrapped in a modern interface is a more comprehensive method for switch monitoring.
Finally, real-time monitoring is crucial to have instant and custom alerts for network issues, allowing IT teams to respond quickly to malfunctions or unusual activity.
Network monitoring with Checkmk includes all this, without forgetting the always vital network port monitoring that is crucial to implement when talking about switches.
What to monitor on a switch?
What needs to be monitored on a switch? Both the general health of the switches themselves, their ports, and the overall traffic. Switch monitoring necessarily includes network port monitoring.
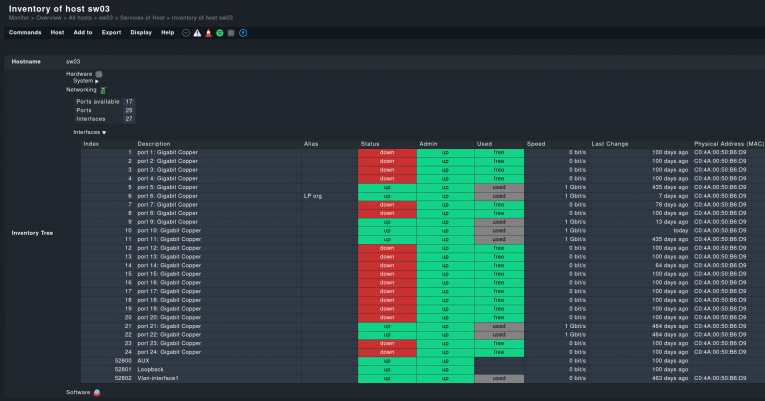
In practice this means the monitoring of a number of metrics. Firstly, each switch port's status, whether they are active or inactive, and why they became so, is important to have highlighted in your monitoring dashboard. Ports that are in use, but should not be, can be a potential security breach, while ports that should be functioning but are not may signal a malfunctioning or a misconfiguration. Network port monitoring can reveal both conditions.
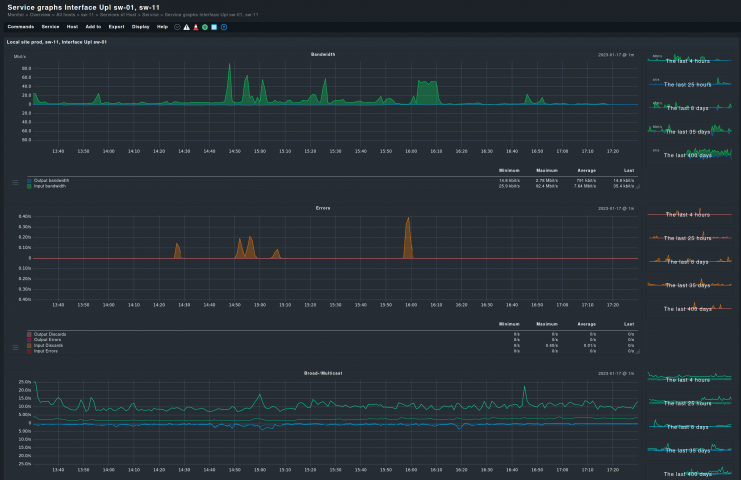
Once the operational status of each switch port is known, it is necessary to know how they are performing. The bandwidth used by each port, along with their packet and error rates, needs to be constantly monitored.
Another important metric to monitor is link utilization. In the context of switch monitoring, link utilization refers to the percentage of a network link’s total bandwidth that is being used over a given period of time. Simply put, it indicates how much of the link’s capacity is currently in use.
Monitoring link utilization helps identify network congestion or under utilized ports, allowing for better resource allocation. This information will tell the administrator how well each port is working, and if there is a possible hardware fault. Traffic analysis and traffic monitoring provide insights into traffic flow, helping to optimize the network's performance and detect abnormal usage patterns. If a port starts discarding packets, it can be a sign of congestion or errors that require immediate attention.
All network interfaces exposed to the switches need to be monitored as well. Here their bandwidth and general usage are two key metrics that can alert you of possible problems.
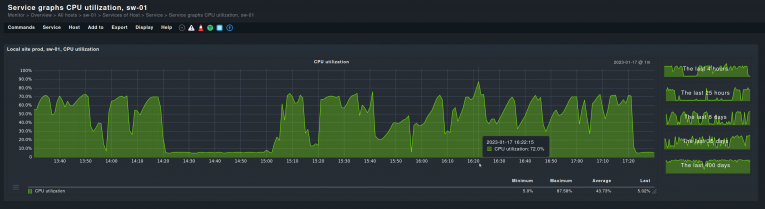
Once ports and network interfaces are under observation, the switches themselves are the next matter. Their overall health, as in CPU average utilization, free memory, operational temperature, is as important as a monitoring of the switch ports. Some of the problems highlighted by port monitoring may be caused by a faulty switch, or an overworked one. Collecting metrics on the switches and not just the ports will give you an optimal view of these network backbones.
Continuous monitoring for switches: Key steps
Keeping an eye on your switches isn’t just a best practice — it’s what keeps the network running smoothly day after day. Continuous monitoring helps you spot issues before they cause trouble and gives you the visibility you need to understand what’s really happening across your infrastructure. Here’s how to get it right from the start.
SNMP switch monitoring and complementary protocols
The first step is choosing a solid monitoring tool that supports SNMP (Simple Network Management Protocol) along with other widely used technologies such as NetFlow, sFlow, and IPFIX. These protocols let your monitoring system collect detailed data from every switch — covering metrics like port status, switch health, memory usage, and CPU load.
Combining SNMP data with flow-based insights gives you both a device-level and traffic-level view of network activity. This means better visibility into bandwidth consumption, congestion points, and switch performance trends across your network infrastructure.
Once your monitoring tool is in place, enable SNMP — or deploy the corresponding agent where needed — on all switches and configure it to collect data from each device.
Monitoring access ports — along with trunk and hybrid ports — for performance and reliability
To make monitoring more precise, create custom checks for specific performance indicators that reflect your environment’s priorities. While access ports are often the main focus, it’s just as important to include trunk and hybrid ports in your monitoring strategy, since issues on these links can affect multiple VLANs and overall traffic flow. Define thresholds for bandwidth usage, port utilization, and packet loss across all critical ports.
Doing so helps minimize false positives and ensures alerts only trigger when something truly requires attention.
Advantages of switch monitoring
Switch monitoring offers a number of advantages. Primarily, knowing how all the switches are performing in your network will help you in capacity planning. Monitoring each switch takes the pulse of a critical part of the network infrastructure; if any switch is overloaded or failing, you may know in advance through the switch monitoring.
If any of a switch’s ports is constantly using up all of the bandwidth or all of the ports on a specific switch, it may be a signal that a node in your network is in need of upgrading or that a rogue user or service is gobbling up all of the traffic. Without network switch monitoring it would be impossible to know about such situations.
Whether any switch is overloaded or failing, monitoring switches will help you know about it beforehand. It is not solely a ‘good to know’ info but can help you prevent network disruptions that can cost time and money. Monitoring each switch and being alerted about unusual usage or errors is the only way to act in advance, before a switch fails altogether or starts to cause service interruptions.
Port monitoring can do the same, and inform you if any switch needs to increase its number of ports. Capacity planning for switch ports is as important as for the complete switches.
Lastly, switch port monitoring can increase the security of your network. Knowing which ports are in use, and need to be enabled, and what are unused, means that a network administrator can block the latter, preventing any potential unauthorized use. In enterprise networks you can never be too safe, and switch monitoring can be of help here too.
What are the challenges of switch monitoring?
Monitoring the great number of switches and ports on a network is always challenging. Tens, even hundreds, of ports all have their own, quickly changing, statuses. Traffic through switches is never static and fluctuates all the time. This can lead to a few challenges.
Ports, and in particular access ports, pose a high risk of generating a flow of false positives. This is because access ports are normally used by users to connect to the network, with their terminals shut down without notice when their job is done. This is seen by the switch monitoring software as a port suddenly going offline, and thus triggering an alert. Of course, it is normal behavior but unless properly pre-configured, the monitoring tool could not know this. Switch monitoring is not implemented without a configuration, and one of its challenges is to set the monitoring up properly at the beginning.
This includes also taking all of the switch ports to be monitored into consideration. A normal port scan is usually not sufficient, as some ports may be momentarily offline during the scan and thus be excluded from the monitoring. These ports will go online sooner or later but if they are not manually added to the monitoring system, you will not notice them. Again, pre-configuration is necessary.
Centralized and rule-based network switch monitoring with Checkmk
Monitoring a switch therefore presents a few challenges that can be often solved by the right configuration. In enterprise networks it is however impractical to manually set up each of the multitude of ports across all the switches. Instead, a monitoring solution that works with a rule-based configuration can show its strength in switch port management. Rules enable the administrator to define a policy for monitoring in a few simple steps and then to monitor only the error rate of all access ports, for example. Network monitoring with Checkmk is rule-based and fits as the right solution to the challenges of switch and port monitoring.
Moreover, complete IT monitoring platforms like Checkmk provide powerful visualizations where administrators can oversee switch performance across multiple locations, detect unauthorized devices, and analyze traffic patterns in real time. This unified visibility supports more informed decisions about hardware upgrades and network optimization.
FAQ
What is a switch monitoring tool?
A network switch monitoring tool is a software that allows administrators to monitor a switch. It often includes network switch management capabilities, which also allows experts to configure switches. These tools may be cloud or on-premise, and generally include port monitoring and network flow monitoring features. Most are paid solutions, but free versions exist, such as Checkmk Raw.
What do bandwidth, packet and error rates mean?
Bandwidth, or network bandwidth to be precise, is the maximum rate of data transfer across a given path, for example, through a switch port. Packet rate is the number of packets per second that move over a network, at a specific point in the network. This may be, again, a switch port or the whole switch. Error rate is the proportion of packets containing one or more errors that have been received over a network.