What is a network protocol?
Network protocols are often named in technical articles, but what are they? Network is easily understandable on its own, protocol as well, but together? What do we mean with “network protocol”?
The ambiguous but accurate answer would be: what allowed you to read this article. I know, not very helpful. But it is the absolute truth.
Network protocols are like languages: they exist to allow communication between different devices and services. Like human languages, you need to have a common language between you and your interlocutor, or you cannot communicate.
There are network protocols for various tasks. All of them allow devices and services to talk to each other, but not all share the same type of content. Since the very first phone line was born, network protocols for sharing files, for printing from a remote printer, or for voice talking have been developed. Literally dozens of network protocols exist nowadays, from the basic and general ones to super-specific ones.
How does a network protocol work?
A network protocol is also called a “communication protocol”, or “network communication protocol”. Technically, a protocol of this class is defined as a set of rules for exchanging information over a network. It is similar to a human language, where the rules are the syntax and grammar of the language, while the info translates to the words we say or write.
Any network protocol works according to certain rules, for a precise scope. The rules deal with “how the info should be transmitted”. They usually establish the order and meaning of some metadata that will tell the receiving device what protocol is being used. Similar to a human conversation, where somebody thanks you, and you know that you should politely reply with “you’re welcome”, network protocols have a set number of expected responses to each type of message.
Not every device supports every protocol, like not every human speaks all languages. For instance, a device may support a network monitoring protocol, while an administrator may need to monitor its functioning. A different device may support a network management protocol because it is meant to manage other devices through one of those protocols.
Unlike human languages that can be all used to speak and write, network protocols are more specific. There are network monitoring protocols that exchange info about the status of a device, to monitor it. Network security protocols securely exchange messages that contain sensitive info (by encrypting them via complicated mathematical algorithms).
Network protocols exist to exchange files (FTP), show web pages (HTTP), connect to a remote device (SSH), monitor and configure it (SNMP), and so on. Some protocols have multiple functions. HTTP, for example, was born to distribute hypermedia texts (commonly called web pages) but has grown into multiple uses, ranging from streaming videos to voice calls.
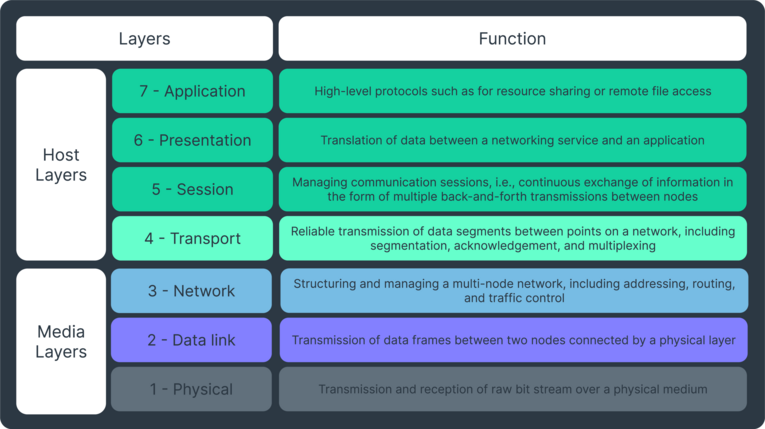
If you’re confused now, don’t worry, the experts felt the same way. Already in the 1970s, when most network systems we use today were being created, the OSI Network Model was developed to facilitate the interoperability between networks by following a system of conceptual layers. There are 7 layers in total, starting from the bottom, the hardware, and ending on the one closest to humans, the application layer. We will match each protocol to the various OSI model layers in the course of this article, when appropriate.
The full list of layers, with an explanation, can be found here.
Who uses network protocols?
I guess you know the answer to this question already: everybody. Network protocols aren’t just for IT specialists and network administrators, since every one of us leverages them in one way or another. Simply browsing the internet, sending an email, receiving an SMS message, or chatting with friends means using a network protocol. Often even more than one at the same time.
Experts have protocols for network monitoring to help them troubleshoot issues in a network, as it’s part of their job. Most people on the other hand won’t use any network monitoring protocols at all. Like natural languages, you learn and use only those that are useful to you. No need to know them all.
But if you are more than an average user, you may want to know which protocols you can use to monitor a network or what network management protocols are out there.
What types of network protocols exist?
There are thousands of network protocols in use today, but we will focus on three main areas: network communication, network management, and network security.
The reason is simple: the first are the most used, and by a great deal. The management ones are what we are more interested in and, last but certainly not least, the security protocols are of primary importance in monitoring.
Network communication protocols
Network communication protocols are the basic type of network protocols, born to transmit info over a network. Thus, they communicate info, be it generic or specific. Most of these protocols are commonly known and the base on which the whole Internet relies.
IP and TCP/UDP
The IP protocol is the root of the Internet. Without it, it wouldn’t have existed in the first place. How it works is easily understood, as its terminology has become part of what we all use to describe the Web.
IP works by delivering packets from a source host to a destination IP address. It is also a routing protocol, as it established the concept of numerical addresses and their various classes. Depending on how the numbers are distributed, a packet can be meant for a local network (LAN) or an external one (WAN). Basically, the Internet is everybody’s WAN.
IP is a connectionless protocol, meaning that there’s no established procedure to start communicating with a host. You just start talking and go on according to the reply (or lack thereof). Connection-oriented protocols instead have a rigid way to start communicating, involving a series of queries and replies that have to be followed for the info to be correctly transmitted and received. An example, built on IP, is TCP (Transmission Control Protocol). You may have heard of TCP/IP. It is so popular that it is being associated with the main network communication protocol of the internet.
The other side of TCP is UDP (User Datagram Protocol). Unlike TCP, UDP is way less rigid, just taking care of how to package messages and sending them as fast as possible. Even though it is generally preferred over TCP for pure speed, you have no guarantee that the other end is correctly receiving your messages, nor actually understanding them.
Among the OSI model layers, IP sits at the number 3, the network. TCP and UDP are above it, at layer 4, transport.
DNS
DNS is another key protocol of the internet. If IP gives every device an address (like a name of a person), DNS (Domain Name System) translates them to a specific position on a network (like the address of your home). DNS is the address registry of the Web, knowing which IP address corresponds to what domain name, and vice versa.
DNS allows you to type a website in the browser and be led to the right one. Internet providers keep a “name server” for their customers that has records of all the IP addresses in their “zone”. The whole internet is divided into lots of these small zones. When you look for a website by its domain, your request moves from the one physically closest to you to the farthest necessary to have a positive answer. Once you have the IP address, the task of DNS is done, and you can move to other network protocols to start sharing the data you wanted.
Perhaps unexpectedly, DNS is at the very top of the OSI layers, the application one, number 7.
HTTP and FTP
We are grouping these together because they have a similar scope. HTTP is usually the next protocol you go to once DNS gives you the IP address matching the domain you sought. HTTP takes care of transmitting the content that resides at that domain. Plain and simple.
FTP does roughly the same. It stands for File Transfer Protocol and, as guessable from the name, focuses on transmitting files instead of webpages. Files can be extremely large, gigabytes and more. Once very popular, it has become less so in recent years as HTTP has taken over most of what FTP once did.
Both HTTP and FTP work over TCP/UDP packets, and are at the application layer of the OSI model.
SMTP
An example of a protocol that is specific for one task only, SMTP (Simple Mail Transfer Protocol) transmits e-mails. And only that. It does not receive e-mails, since other protocols do that instead. SMTP only sends them.
One task only, but done so well that it has been the network protocol for it since the early 1980s. SMTP not only sends your e-mails but adds the necessary headers (the "From" and "To" fields in e-mails are headers), and makes sure that the recipient has received the mail. Similarly to TCP, there are different requests to ensure proper sending and receiving of messages.
SMTP is another protocol of the application layer of the OSI model.
Network management protocols
Over the years, the need to manage devices has grown alongside the size of networks. What was once a handful of computers, all in the same room, has become tens or hundreds of them, scattered in multiple locations worldwide, often under more than one organization.
Managing them all is a difficult task. Network management protocols were developed to specifically ease that burden.
SNMP
As we have talked about Simple Network Management Protocol (SNMP) before, a long explanation is unnecessary. Suffice to say, SNMP is the granddad of network management protocols, hailing from the early 1980s and still largely used today. Many alternatives exist, though, which we discuss elsewhere.
Its function is twofold: it not only manages (configures) remote devices, but can be used for network monitoring as well. The protocol is based on the concept of a manager and an agent. The first manages the various devices on which the agents are installed and keeps track of all collected metrics. Agents keep an eye on the device they are on and may send an alert to the manager if something is off.
These are the basics of a fairly complex protocol. SNMP has been the main network monitoring protocol for over 4 decades. It is present on the OSI model at layer 7, application.
Network security protocols
In this section, we will see a few network protocols that focus on ensuring secure communication. They are not like human languages but more like a code that is preemptively exchanged between two people, where a symbol or number means something only to those who know the code.
Network security protocols are the equivalent of such codes in computers.
SSL and TLS
SSL (Secure Sockets Layer) is indeed a layer over other protocols. Commonly, it is used with HTTP, making it HTTPS (S for secure). SSL was born in 1995 to provide a way to securely transmit info in the Netscape browser. Since then, all browsers have implemented it.
How does it work though? It encrypts all data transmitted by using a combination of cryptographic keys and public certificates, along with a hashing algorithm. Lots of new words that can be easily translated: two computers agree, automatically, on how to encrypt the data they are going to exchange. The server provides its digital certificate, a file containing a long alphanumeric string representing the identity of the server. The client then knows that the server is who it claims to be, as only that server should have that specific certificate. After that, a couple of keys (other alphanumeric files) are generated based on the certificate and used to mathematically encrypt all the data transferred from then on.
Sounds like a lot of complicated steps, but everything is transparent to the user. No step is manual, all is automatic.
SSL was plagued with flaws and security issues from the beginning. It is now deprecated in favor of a more robust network security protocol, TLS (Transport Layer Security). It does exactly the same as SSL, just more safely.
Curiously, neither SSL nor TLS fit clearly in the OSI model layers. They are supposed to be somewhere between the fourth and fifth, the transport and session layers.
SSH
Along the same years as SSL, the network security protocol SSH (Secure Shell Protocol) was also developed. SSH works in concept similar to SSL/TLS: a client and a server exchange a set of keys and/or certificates to encrypt the data they’re exchanging.
We said “or” as with SSH it is not necessary to have a digital certificate. Authentication can be done via the typical pair of username and password, and then only digital keys are used. The certificate under SSH is useful to automatically authenticate, without a user present to type the name and password.
SSH is thus a bit more flexible than SSL/TLS. It is usually not solely used as a network security protocol, but also as a protocol for monitoring network health. It can be considered as one of the network monitoring protocols as well. This is because SSH gives complete access to a remote computer, not just exchanging encrypted data. Once access is granted, you can manage, configure, and monitor the remote computer like it was yours. SSH is a great example of a network protocol that has more than one use.
SSH is on the OSI model at layer 7, application.
IPSec
IPSec stands for Internet Protocol Security and the name should already tell you where it sits in the OSI model layer. It is the equivalent to IP, but secure. Thus, it is very low, at layer 3.
You probably have not heard of IPSec per se, but of its most famous use: VPN. A virtual private network is like having remote computers like they were in your network, close to you. That works because IPSec takes care of creating a “tunnel”, an encrypted communication between computers, joining them virtually together as if they were physically close.
The tunnel is established similarly to how SSH and SSL work, so no big surprises here. However, it is not used to exchange data with random servers, like SSL/TLS, or to access them, like SSH, but to have secure communication with multiple servers. That’s the definition of a VPN. IPSec is the network communication and security protocol that allows a VPN to work. It is typically used by companies to protect the communication among all the computers in their organization, even if they can’t physically be on the same network.
What is a network monitoring protocol?
Another type of network protocols that focus on one task are network monitoring protocols. They are subtypes of network communication protocols because, after all, they also exchange info. But whereas those are generic, network monitoring protocols are all about transmitting data that can be used by a network administrator to identify issues in the network.
Compared with a human language, they are like people who regularly communicate with their doctors how they feel, and the doctor interprets their words to come up with a cure, if needed.
Which protocol can be used for network monitoring?
SNMP is probably the main one. It is often a good answer to the which protocol can be used for network monitor question. However, it is not the only one. A handful of other network monitoring protocols are a worthy choice as well.
NetFlow and IPFIX
Cisco’s proprietary NetFlow was the main competitor to SNMP in network monitoring for years. It is now superseded by IPFIX (IP Flow Information Export), which is based on it. Both protocols are “focused” network communication protocols as well. Focused, because instead of collecting everything that is being transmitted between network devices, they only collect parts of it. This way, they have a general idea of where traffic is coming from and going to. These parts are called “flows”. Compared to human languages, these flows are like talking in broad, general concepts and ideas instead of going into detail.
For network monitoring, it can be advantageous to only have a general idea of how traffic moves. It eases the troubleshooting of issues and bottlenecks, initially. It is always possible to delve deeper in the info NetFlow and IPFIX captured as flows later, if desired.
WMI and MI
A popular choice for network monitoring under Windows is WMI (Windows Management Instrumentation). A fairly complex network monitoring protocol, WMI is similar in scope to a hybrid of SSH and SNMP. It allows both to access metrics to monitor a device and to have full access to it. Thus, powerful. It doesn’t have the security aspects of SSH, though, so it is not a network security protocol.
WMI has morphed into MI (Management Infrastructure), supported by all the recent Windows’ versions. It works very similar to WMI but addresses some issues the original Windows-based network monitoring protocol had.
ICMP
A barebone network monitoring protocol is ICMP. An acronym for Internet Control Message Protocol, it is one of the oldest and simplest network protocols. It sits at a low OSI model layer, number 3, along with IP, and it hails from the same technological era.
Its simplicity is its strength. All ICMP takes care of is checking that a device is up and replying. It is like two people repeatedly checking on each other with “are you there?”. The answer, in the case of ICMP, is either yes or no answer at all. In this case, an issue may be present and may be worth investigating further. It is nothing fancy, but for a first step in troubleshooting possible network problems, ICMP works just fine.